SpringMvc xss (CVE-2014-1904)学习与分析
介绍
https://pivotal.io/cn/security/cve-2014-1904 根据漏洞描述: 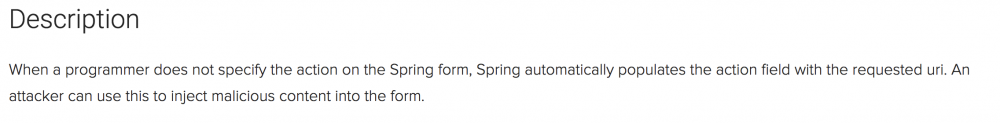
内容
可以知道需要用form标签,选择3.2.8版本以前的spring-mvc。然后写了一个demo,代码如下:
bean
````
package net.codersec.entity;
public String getUsername() {
return username;
}
public void setUsername(String username) {
this.username = username;
}
public String getPassword() {
return password;
}
public void setPassword(String password) {
this.password = password;
}
}
````
controller
````
package net.codersec.controller;
import net.codersec.entity.User;
import org.springframework.stereotype.Controller;
import org.springframework.ui.Model;
import org.springframework.web.bind.annotation.RequestMapping;
/**
* Created by bsmali4 on 18/1/25.
*/
@Controller
public class UseController {
@RequestMapping(value = "/login/*")
public String login(Model model){
model.addAttribute("user", new User());
return "login";
}
}
````
其中标签需要绑定一个bean,其在form的commandName属性绑定
```
<%@ page language="java" contentType="text/html; charset=UTF-8" pageEncoding="UTF-8"%>
<%@ taglib prefix="form" uri="http://www.springframework.org/tags/form" %>
<html>
<body>
<h2>Hello,welcome to CVE-2014-1904!</h2>
<form:form method="post" commandName="user">
<form:input path="username"/>
<form:input path="password"/>
<input type="submit" value="login"/>
</form:form>
</body>
</html>
````
这里需要说明一个特性,在form:form中未设置action的时候,spring-mvc会自动将当前url设置为action,比如
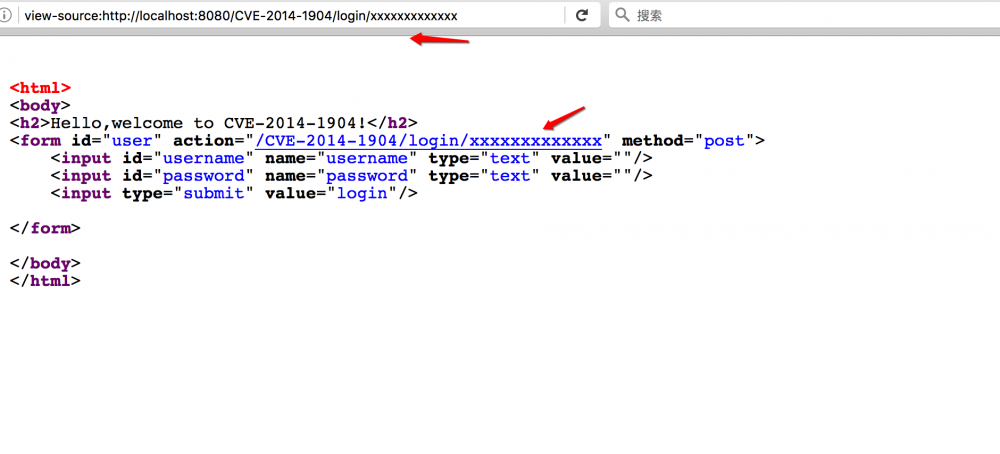 如果没有过滤的话会造成一个xss
如果没有过滤的话会造成一个xss
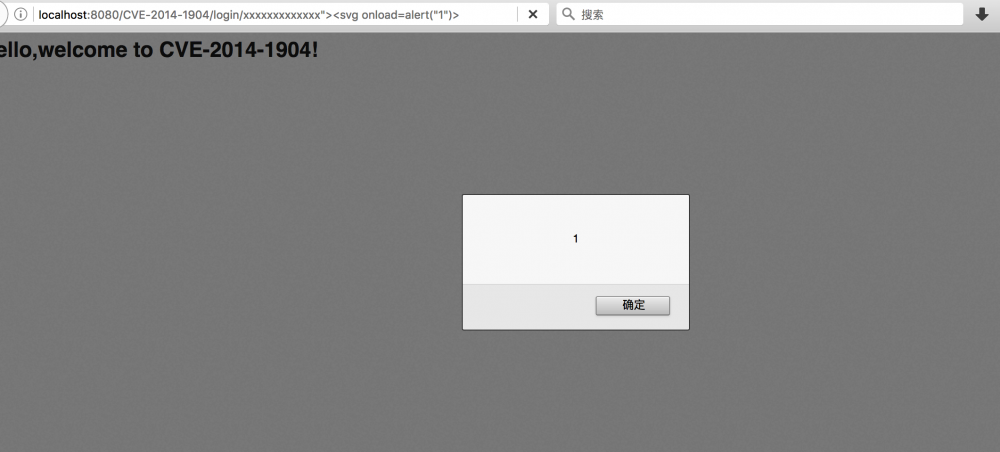
 如果没有过滤的话会造成一个xss
如果没有过滤的话会造成一个xss

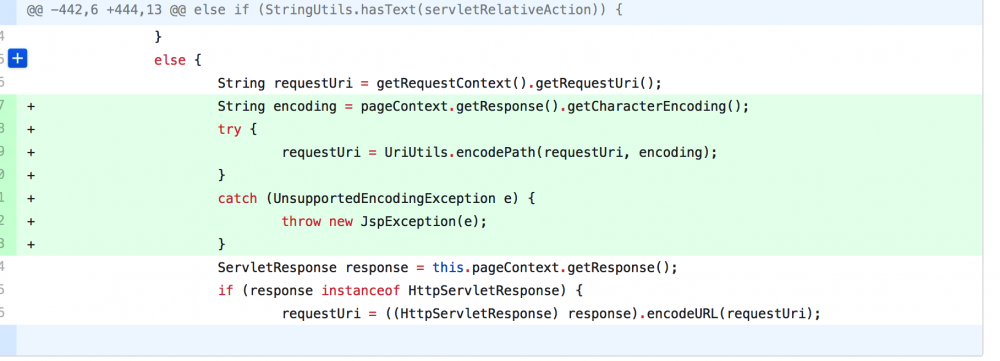
官方在3.2.8版本修复补丁如下 在org/springframework/web/servlet/tags/form/FormTag.java位置

其实就是url转码了一次,怎么绕过,大家可以自己试试?我试了几种常见的方式没有绕过去,如果大家有想法,欢迎一起交流。本文权当笔记纪录,文字很不严谨,如有错误,欢迎提出来。
参考文档
https://github.com/spring-projects/spring-framework/commit/741b4b229ae032bd17175b46f98673ce0bd2d485 https://www.cnblogs.com/Summer7C/p/4713190.html
正文到此结束
热门推荐
相关文章
Loading...











![[HBLOG]公众号](https://www.liuhaihua.cn/img/qrcode_gzh.jpg)

