Java:Shiro的架构学习笔记
张开涛的第一章 Shiro简介——《跟我学Shiro》,其实是解读了一下 Shiro的架构 这篇文章,本着寻根究底的态度,我再一次去阅读这篇文章。为什么说是再一次呢?因为之前读过好几次了,不过就是没有完全理解明白,自己也说不好卡在哪里了,包括张开涛的文章,我也读过两遍了,这次第三遍读,一下子豁然开朗,然后不明白之前为啥就没读明白。
正文
3个主要的概念: Subject , SecurityManager 和 Realms 。
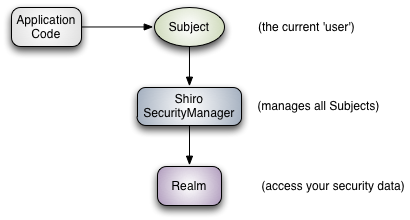
Subject 可以是一个用户,但不仅仅可以代表一个用户,所有对这个系统的外部请求的主体都可以看成是一个 Subject ,例如一个 service ,这里是做了一个抽象概括的设计,这个我能理解,如果你理解不了的话,那说明你还没有接触过相关的业务,例如 SSO ,那就先把它理解成一个用户,也没有关系。将来总有一天,你会明白,会回来和我一起唱这首《当当当》。
SecurityManager Shiro设计的核心的逻辑都在这里面,但是,我们应该可以先不理会它是怎么工作的,先把它当做一个黑匣子,它有它自己运行的逻辑。
Realms 这个单词的意思是领域,范围。原文这么说:
Realms act as the ‘bridge’ or ‘connector’ between Shiro and your application’s security data. When it comes time to actually interact with security-related data like user accounts to perform authentication (login) and authorization (access control), Shiro looks up many of these things from one or more Realms configured for an application.
In this sense a Realm is essentially a security-specific DAO: it encapsulates connection details for data sources and makes the associated data available to Shiro as needed. When configuring Shiro, you must specify at least one Realm to use for authentication and/or authorization. The SecurityManager may be configured with multiple Realms, but at least one is required.
就是说和安全相关数据( security-specific )打交道的是这个对象,有关认证、授权都是通过它来打交道,或者说,通过不同的realm来和相关的“机构”(打个比方)打交道,每个机构有自己的 realm ,再或者说, realm 可以理解成 DAO ,去访问相关的数据。
更具体的分析:
Subject:A security-specific ‘view’ of the entity (user, 3rd-party service, cron job, etc) currently interacting with the software.
一个实体的安全相关的 view –这个概念还需要好好理解一下,怎么被称为一个 view 呢?
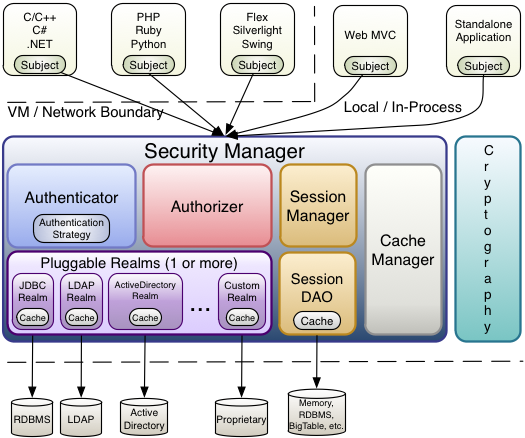
SecurityManager又分为了一些子模块:
Authenticator (org.apache.shiro.authc.Authenticator) The Authenticator is the component that is responsible for executing and reacting to authentication (log-in) attempts by users. When a user tries to log-in, that logic is executed by the Authenticator. The Authenticator knows how to coordinate with one or more Realms that store relevant user/account information. The data obtained from these Realms is used to verify the user’s identity to guarantee the user really is who they say they are. Authentication Strategy (org.apache.shiro.authc.pam.AuthenticationStrategy) If more than one Realm is configured, the AuthenticationStrategy will coordinate the Realms to determine the conditions under which an authentication attempt succeeds or fails (for example, if one realm succeeds but others fail, is the attempt successful? Must all realms succeed? Only the first?).
Authenticator:认证器,用来负责用户登录认证,它对应着一个或者多个 Realm 。
Authentication Strategy:认证策略,如果多个 Realm 被配置,那么 Authentication Strategy 来负责协调这些 Realm 产生矛盾的时候,该如何处理,例如一个 realm 成功,而其它的失败了,改怎么办,等等。在这一点上,张开涛的文章解释的不是太准确。
Authrizer:授权器,负责确认用户的访问权限。
SessionManager (org.apache.shiro.session.mgt.SessionManager) The SessionManager knows how to create and manage user Session lifecycles to provide a robust Session experience for users in all environments. This is a unique feature in the world of security frameworks - Shiro has the ability to natively manage user Sessions in any environment, even if there is no Web/Servlet or EJB container available. By default, Shiro will use an existing session mechanism if available, (e.g. Servlet Container), but if there isn’t one, such as in a standalone application or non-web environment, it will use its built-in enterprise session management to offer the same programming experience. The SessionDAO exists to allow any datasource to be used to persist sessions. SessionDAO (org.apache.shiro.session.mgt.eis.SessionDAO) The SessionDAO performs Session persistence (CRUD) operations on behalf of the SessionManager. This allows any data store to be plugged in to the Session Management infrastructure.
SessionManager : session 管理器, Shiro 没有完全依赖 HTTP 的 session ,而是设计了一个独立的 session 。
SessionDAO : session 的 DAO ,用来处理session数据的保存。
CacheManager :缓存管理器。
Cryptography :加密模块。
Realms: 上面介绍过。
SecurityManager
这个是核心,需要反复理解的是这个,下面又用了一些篇幅来介绍这个,不过在没有完全实践之前,总还是不明白,所以就先不总结了。
总结
又阅读了一遍架构这篇文章,结合着张开涛的文章,感觉明白了不少,现在感觉 Shiro 还是挺简单的,有个两三天应该就大体理解了,不明白当时怎么就堵住了,陷入了思维的死胡同。
- 本文标签: dataSource Persistence struct session 管理 entity apache ORM 安全 总结 Job ip bus IDE src java Service cat HTML 文章 servlet id 数据 example rmi Security 加密 App Enterprise 认证 IO UI Connection Authorization https 缓存 CTO http web cache 配置
- 版权声明: 本文为互联网转载文章,出处已在文章中说明(部分除外)。如果侵权,请联系本站长删除,谢谢。
- 本文海报: 生成海报一 生成海报二











![[HBLOG]公众号](https://www.liuhaihua.cn/img/qrcode_gzh.jpg)

