基于 Spring Security 和 JWT 的权限系统
Token到底如何实现,才是最好的方式?
身经百个项目(.(▼へ▼メ)装逼.) 见过不少项目是这样实现的
- token?我们不需要
- token写死的,后台提供给客户端(确实有不少)
- token动态,后台通过某些算法生成token,提供给客户端(这种方式不是不行,只是不够完美)
- 整个JSON数据加密传输,后台提供密钥(em....不评价)
- 等等
三、解决方案
今天要讲解的是采用 JWT ,解决Token问题
#科普一下JWT
JSON Web Token (JWT)是在网络应用间传递信息的一种基于JSON的开放标准 (RFC 7519) ,用于作为JSON对象在不同系统之间进行安全地信息传输。主要使用场景一般是用来在 身份提供者和服务提供者间传递被认证的用户身份信息。
JWT由三部分组成,依次如下:
- Header(头部) 包含两部分:token类型和采用的签名算法
- Payload(负载) 是Token携带的用户自定义内容,数据是base64,非加密,可破解,不能存敏感信息;内容越多,token越长
- Signature(签名) 将Header+Payload组成一个字符串,通过指定的签名算法进行计算,得到一个签名值,服务端可通过这个标志,来判断Token是否合法
#讲解Spring Security(附赠)
有JWT解决Token问题,再结合Spring Security 可以解决用户权限模块重重问题(真的很强大),当然除了Spring Security,还有Apache Shiro也可以解决权限,但没有Security强大,后续将写篇文章详解对比两者。
四、实现方式
pom.xml中引入 JWT 和 Spring Security 的依赖 jar
<dependency>
<groupId>org.springframework.boot</groupId>
<artifactId>spring-boot-starter-security</artifactId>
</dependency>
<dependency>
<groupId>io.jsonwebtoken</groupId>
<artifactId>jjwt</artifactId>
<version>0.9.1</version>
</dependency>
复制代码
JWT工具类,生成Token、验证Token、刷新Token等
@Component
public class JwtTokenUtil {
private static final String CLAIM_KEY_USERNAME = "sub";
private static final String CLAIM_KEY_CREATED = "created";
// 生成token
public String generateToken(UserDetails userDetails) {
...
}
// 刷新token
public String refreshToken(String token) {
...
}
// 校验token
public Boolean validateToken(String token, UserDetails userDetails) {
...
}
复制代码
Token过滤器, 处理接口的token
@Component
public class JwtTokenFilter extends OncePerRequestFilter {
@Autowired
private UserDetailsService userDetailsService;
@Autowired
private JwtTokenUtil jwtTokenUtil;
@Override
protected void doFilterInternal (HttpServletRequest request, HttpServletResponse response, FilterChain chain) throws ServletException, IOException {
String authHeader = request.getHeader(Constant.HEADER_STRING );
if (authHeader != null && authHeader.startsWith(Constant.TOKEN_PREFIX )) {
final String authToken = authHeader.substring(Constant.TOKEN_PREFIX.length() );
String username = jwtTokenUtil.getUsernameFromToken(authToken);
if (username != null && SecurityContextHolder.getContext().getAuthentication() == null) {
UserDetails userDetails = this.userDetailsService.loadUserByUsername(username);
if (jwtTokenUtil.validateToken(authToken, userDetails)) {
UsernamePasswordAuthenticationToken authentication = new UsernamePasswordAuthenticationToken(
userDetails, null, userDetails.getAuthorities());
authentication.setDetails(new WebAuthenticationDetailsSource().buildDetails(
request));
SecurityContextHolder.getContext().setAuthentication(authentication);
}
}
}
chain.doFilter(request, response);
}
}
复制代码
Spring Security的核心配置
@Configuration
@EnableWebSecurity
@EnableGlobalMethodSecurity(prePostEnabled=true, securedEnabled = true)
public class WebSecurityConfig extends WebSecurityConfigurerAdapter {
@Autowired
private UserDetailsServiceImpl userService;
@Bean
public JwtTokenFilter authenticationTokenFilterBean() throws Exception {
return new JwtTokenFilter();
}
@Bean
public AuthenticationManager authenticationManagerBean() throws Exception {
return super.authenticationManagerBean();
}
@Override
protected void configure(AuthenticationManagerBuilder auth) throws Exception {
auth.userDetailsService(userService).passwordEncoder(new BCryptPasswordEncoder());
}
@Override
protected void configure(HttpSecurity httpSecurity) throws Exception {
String[] urls = new String[]{"/user/login", "/user/register"};
httpSecurity.csrf().disable()
.sessionManagement().sessionCreationPolicy(SessionCreationPolicy.STATELESS).and()
.authorizeRequests()
// 允许注册和登录接口不需token访问
.antMatchers(urls).permitAll()
.anyRequest().authenticated();
httpSecurity.addFilterBefore(authenticationTokenFilterBean(), UsernamePasswordAuthenticationFilter.class);
httpSecurity.headers().cacheControl();
}
}
复制代码
权限测试,接口需要限制访问限制,则添加 @PreAuthorize
@RestController
public class RoleController {
/**
* 测试普通权限
*
* @return
*/
@PreAuthorize("hasAuthority('ROLE_NORMAL')")
@GetMapping(value="/normal/test")
public String test1() {
return "普通角色访问";
}
/**
* 测试管理员权限
*
* @return
*/
@PreAuthorize("hasAuthority('ROLE_ADMIN')")
@GetMapping(value = "/admin/test")
public String test2() {
return "管理员访问";
}
}
复制代码
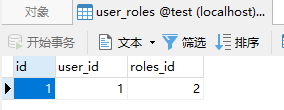
需给用户添加角色才能访问,如下图 用户角色关系表
正文到此结束
- 本文标签: UI key 测试 Security cat Spring Security 代码 build ORM 配置 XML web 文章 tar id 管理 final pom bean map 加密 json apache Word js 服务端 IDE REST authenticate constant 安全 session URLs http spring https IO 数据 value 认证 Service 密钥 token App src rmi servlet cache
- 版权声明: 本文为互联网转载文章,出处已在文章中说明(部分除外)。如果侵权,请联系本站长删除,谢谢。
- 本文海报: 生成海报一 生成海报二
热门推荐
相关文章
Loading...










![[HBLOG]公众号](https://www.liuhaihua.cn/img/qrcode_gzh.jpg)

